Stay Informed.
BackBox Linux vs. BlackArch Linux vs. ArchStrike – Full Breakdown In 2025
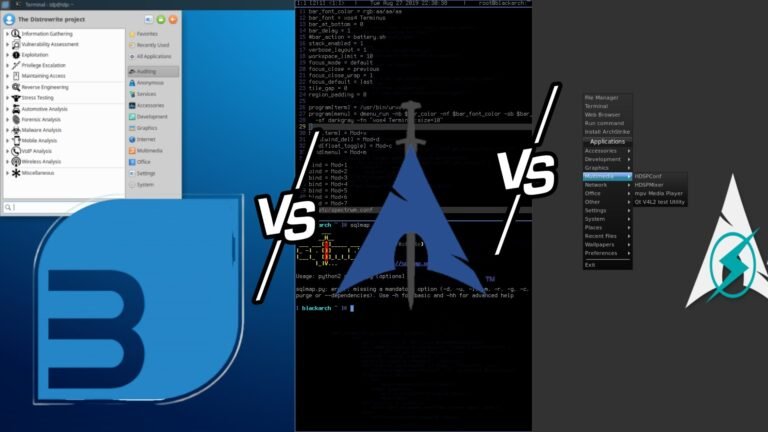
If you’re choosing between BackBox Linux vs. BlackArch Linux vs. ArchStrike, you want a distro that matches the way you work / whether that’s quick lab work, full-scale red-team ops, or learning the command line while keeping your desktop usable.…
What Is Endpoint Detection and Response – EDR Security

What Is Endpoint Detection and Response In today’s extremely complicated cyber security environment, where advanced threats are everywhere, old-fashioned endpoint protection is not enough. Endpoint Detection and Response (EDR) security comes up as a quite strong and holistic answer to…
Is it Illegal To Access The Dark Web? 2025

Is it Legal to Browse the Dark Web? The dark web encompasses all of these which are extremely very few misunderstood and very mystified parts of the internet. There is intrigue, secrecy, and suspicion all around this dark web. But…
How to Protect Yourself While Browsing the Dark Web Safely in 2025/2024: Step by Step

The web is an ever-darkening place, full of mystery and danger. Yet most people come online to take advantages such as the anonymity, which grants access to information that is otherwise unavailable through the surface web. It can serve as…
Is Disposable 10-Minute Mail Trackable? Myths and Realities Explored – 2025

Have you ever had the wish of not sharing your real email address and still doing things on the internet? Business sites, such as 10-Minute Mail, make it very easy to create disposable email addresses that disappear after a short…
What Is npcap? Full Guide to Essential Network Capturing Tool In 2025

Nmap Packet Capture is more critical than ever that one actually understands network traffic and is able to monitor it, be it a network administrator, a cybersecurity expert, or a developer building applications against network data. You need some solid…
Top 10 Search Engines in the Deep Web and Dark Web

Discovering hidden corners of the net that Google or Bing cannot reach has always been a thought in your mind. The Deep Web and Dark Web are secret worlds waiting to be explored. In this guide, we are going to…
Top 20 Cybersecurity Companies to Watch in 2024

Cybersecurity Companies With the continuous evolution of the cyberspace, the demand for adequate information technology security is on the increase. This has also led to the emergence of several companies equipped with the latest technologies and services. In this publication,…
Key Differences Between IAM & PAM Solutions: Comprehensive Comparison

Understanding IAM and PAM Solutions In the realm of cybersecurity, it is imperative to manage the access to sensitive data streams. IAM and PAM are terms which are used to audit and complement access to the resources. However, they can…
Kali Linux vs Parrot OS: 5 Major Differences That Impact Your Security

If you’ve ever dipped your toes into the world of cybersecurity, you’ve probably come across Kali Linux and Parrot OS. Both are celebrated Linux distributions renowned for their comprehensive security toolkits and their roles in penetration testing, digital forensics, and…




