Stay Informed.
VPN vs Tor vs Proxy. What Are The Differences? In 2025

when searched for vpn vs tor vs proxy, you’re probably trying to figure out which tool will actually solve your problem: hide your browsing from a flaky cafeeh Wi-Fi, access Netflix from another country, or protect your identity while researching…
Resolving the Issue of uTorrent Software Being Detected as a Virus 2025

Fixing uTorrent Being Detected as a Virus Issue When it comes to downloading files via torrent, torrent download programs have become extremely popular. Among these programs, uTorrent is one of the most common. However, just because it is popular and…
How Is The Internet Useful For Students

Why is the Internet Important for Students? The network indeed has shaped students’ lives and reshaped education completely; learning outside conventional classrooms is no longer possible. The role of the internet in academic study was very crucial long before the…
What Are Visual Language models (VLMs) And How Do They Work?
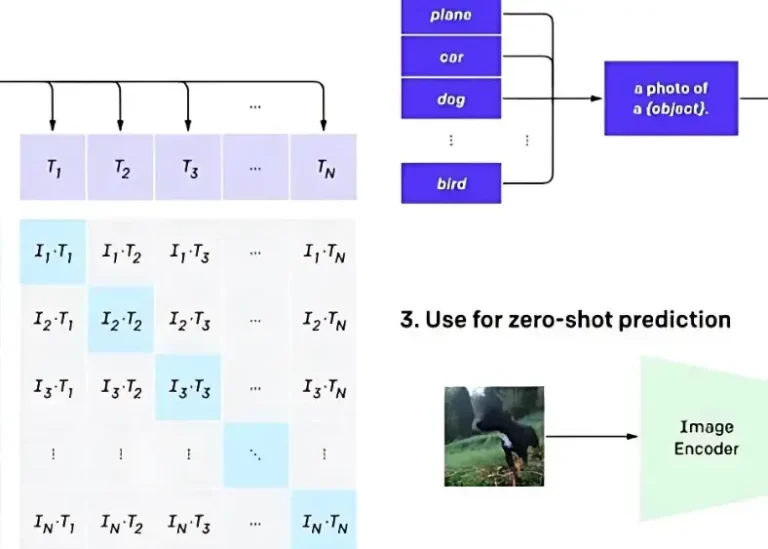
According to reports, 80% of the data is visual. Companies like Google and Microsoft use Visual Language Models (VLMs) to comprehend it better. Such VLMs would enable learning from images as well as texts. It has some assistance for visual…
What Is Sudo Command in Linux? How to Use It + Examples 2025
Did you know that millions of Linux users around the world make use of the sudo command? It enables them to manipulate files and use features that demand additional privileges. This specific command is very essential in efficiently managing your Linux…
Top 10 Search Engines in the Deep Web and Dark Web

Discovering hidden corners of the net that Google or Bing cannot reach has always been a thought in your mind. The Deep Web and Dark Web are secret worlds waiting to be explored. In this guide, we are going to…
Understanding GPL License & Risks of Using Nulled WordPress Themes and Plugins

Understanding the GPL License A base for free software licenses is known as GNU General Public License (GPL), which allows users to use, modify, and redistribute software. This offers significance not only to the developers of software but also to…
How to Access the Deep Web with the TOR Browser in 2025 on Any Device

Browsing the deep web using the TOR browser Network is a well-known activity for accessing information, communicating with other people, or even conducting business transactions. However, there exists a phenomenon on the network that is both fascinating and disturbing known…
How to Get Google Cybersecurity Certified and Boost Your IT Career
Overview of Google Cybersecurity Certification In the context of pursuing career advancements in the rapidly changing technological environment, getting a Google Cybersecurity Certification is regarded as a key asset. Hence, it is important to analyze the significance and the merits…




