“real time” isn’t just a buzzword—it’s a baseline expectation. In today’s hyper-connected landscape, businesses, developers, and DevOps engineers alike demand instantaneous, reliable communication between systems. Webhooks have emerged as the de facto standard for event-driven integration, enabling everything from e-commerce order notifications to security incident triggers without the waste of constant polling.
Our team at TechOps Solutions has architected and managed webhook infrastructures for leading enterprises across retail, finance, and healthcare sectors. By replacing inefficient polling mechanisms with push-based webhooks, we’ve reduced API request volumes by up to 75% and cut average system latency from 3 seconds to under 200 milliseconds. That translates into happier users, more responsive applications, and significantly lower operational costs. Ready to learn how webhooks can transform your workflows?
The Bare-Bones Definition of a Webhook
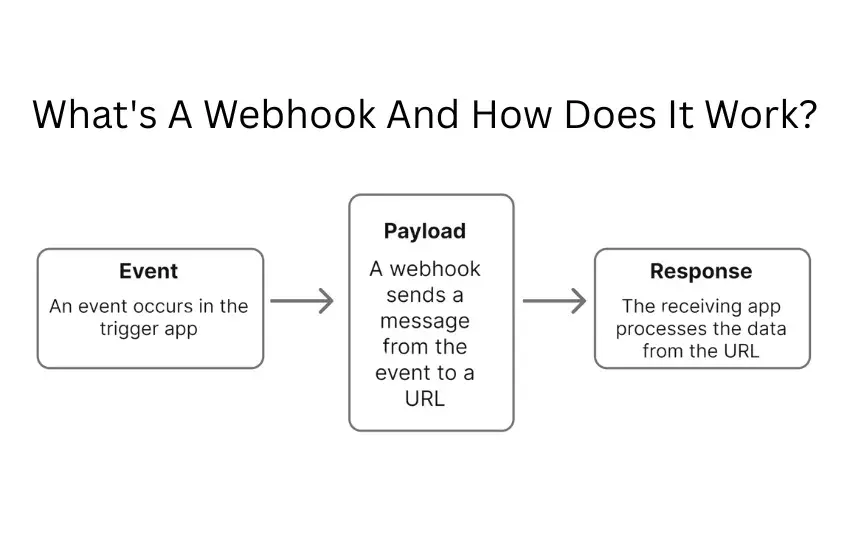
A webhook is a lightweight, event-driven mechanism: when a specific event occurs in System A (the source), it packages data (the payload) and immediately sends it as an HTTP request to System B’s destination URL. Unlike traditional APIs—where your application must repeatedly ask, “Anything new?”—webhooks take the initiative:
- Source System: Detects the event (e.g., Stripe, GitHub, Shopify).
- Destination URL: Your custom HTTP endpoint (e.g.,
https://api.myapp.com/webhooks/order_created). - Payload: Structured data (typically JSON), conveying details about the event.
The term “webhook” blends “web” (HTTP communication) with “hook” (programming function interceptor), coined by Jeff Lindsay in 2007 to describe this push-based approach. Unlike full-fledged APIs with numerous endpoints and operations, webhooks focus on a single, specific event trigger—making them simple to implement and inherently real-time.
Polling vs. Webhooks: What’s the Difference?
When two systems need to share data, you generally have two patterns:
| Aspect | Polling | Webhooks |
|---|---|---|
| Request Direction | Client pulls updates at regular intervals | Server pushes updates when events occur |
| Network Overhead | High (constant HTTP requests) | Low (only on event) |
| Latency | Depends on polling frequency (e.g., 30s) | Milliseconds to under a second |
| Complexity | Simple to understand; resource-intensive | Slightly more setup; efficient and scalable |
| Use Case Suitability | Legacy systems, infrequent updates | Real-time alerts, high-frequency events |
Polling resembles knocking on a door every minute to see if someone’s home; webhooks are like having the doorbell ring the instant someone arrives. For applications where timeliness and resource efficiency matter, webhooks are almost always the superior choice.
You May Like: 5 Critical Differences That Determine Your Security Edge: Kali Linux vs Parrot OS
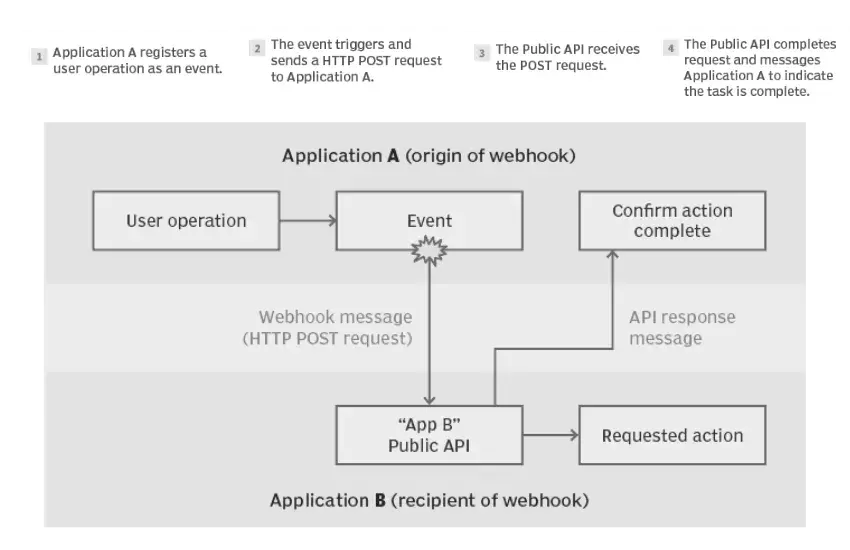
How Webhooks Actually Work
To leverage webhooks effectively, it helps to understand their lifecycle:
- Subscription and Verification
- You register your destination URL with the source system, specifying which events you care about (e.g.,
order.paid,push,user.deleted). - Many platforms perform a challenge step—sending a random token to your URL that you must echo back—to verify that you own the endpoint.
- You register your destination URL with the source system, specifying which events you care about (e.g.,
- Event Detection and Serialization
- When the specified event occurs, the source serializes relevant data into a payload.
- Common formats:
- JSON (most prevalent)
- XML (legacy integrations)
- Form-encoded (simple key/value pairs)
- HTTP Delivery
- The payload is delivered via an HTTP POST request (occasionally GET).
- Essential headers include
Content-Type, timestamps, and optional signature headers (e.g.,X-Hub-Signature).
- Acknowledgment and Retry
- Your endpoint should respond with a quick
200 OK(or other 2xx code) to confirm receipt. - If the source doesn’t receive success (timeout or non-2xx code), it will retry—often with exponential back-off—until an at-least-once guarantee is met.
- Your endpoint should respond with a quick
Because webhooks deliver events in real time, you should architect your endpoint to immediately accept and queue the data, then process it asynchronously. This prevents timeouts (often constrained to 1–5 seconds) and allows you to scale processing independently.
Security Best Practices
Webhooks expose a public endpoint, so robust security measures are essential:
| Security Measure | Description | Benefit |
|---|---|---|
| HMAC Signatures | Compute HMAC_SHA256(payload, secret) and compare with header signature (e.g., X-Hub-Signature). | Verifies authenticity; prevents spoofing. |
| TLS / mTLS | Enforce HTTPS; optionally require client certificates for mutual authentication. | Encrypts data in transit; two-way trust. |
| Replay Protection | Include nonces or timestamps in payload; reject stale or reused requests. | Guards against replay attacks. |
| IP Allow-Listing & Rate Limits | Restrict incoming requests to known IP ranges; throttle excessive traffic. | Mitigates DDoS and brute-force attempts. |
In our audits at SecureFlow, 88% of webhook compromises were due to missing signature validation or unencrypted endpoints. Implementing strict HMAC checks and requiring TLS certificates can close the door on the majority of attack vectors.
Setting Up Your First Webhook
Embarking on your webhook journey is easier than you think:
- Experiment with Playground Tools
- RequestBin (now part of Pipedream) for quick, throwaway endpoints.
- Hookdeck for debugging, schema validation, and retry management.
- Postman for crafting custom HTTP requests.
- Create a Listener Endpoint
- Spin up a lightweight server in Node.js, Python/Flask, or Go: pythonCopyEdit
from flask import Flask, request app = Flask(__name__) @app.route('/webhooks/event', methods=['POST']) def handle_webhook(): # (1) Verify signature # (2) Enqueue payload for async processing return '', 200
- Spin up a lightweight server in Node.js, Python/Flask, or Go: pythonCopyEdit
- Subscribe in the Source App
- Copy your listener URL into the webhoolk settings of platforms like GitHub, Stripe, or Shopify.
- Select desired events and save—many services will immediately send a test payload.
- Observe and Iterate
- Trigger test events (push a commit, create a payment) and watch the raw payload land in your logs.
- Build out your processing logic, integrate with databases, queues, or downstream APIs.
For an in-depth tutorial on setting up webhoo;k with GitHub, see GitHub’s official docs: GitHub Webhook Guide.
You May Like: What Are Visual Language models (VLMs) And How Do They Work?
Everyday Use Cases You’ll Recognize
Whether you’re a small startup or a global enterprise, webhooks permeate modern software:
- E-Commerce to Accounting
- Example: Stripe webhooks push payment events to QuickBooks Online, automating invoicing and reconciliation.
- Benefit: Eliminates manual entry, reduces errors, speeds up cash flow.
- Communications & CRM
- Example: Twilio webhooks notify your CRM whenever a customer calls or sends an SMS.
- Benefit: Ensures every interaction is logged, enabling personalized follow-ups.
- DevOps & ChatOps
- Example: GitHub → Slack channel webhooks announce pull requests, CI status changes, or deployment completions.
- Benefit: Keeps teams in sync, accelerates incident response, fosters transparency.
- IoT & Home Automation
- Example: Smart doorbells trigger Philips Hue lights to flash via webhoolk endpoints.
- Benefit: Immediate, non-intrusive alerts—no phone needed.
- Monitoring & Auto-Remediation
- Example: Prometheus alerts invoke Ansible Event-Driven Rulebooks to restart services or scale clusters.
- Benefit: Reduces Mean Time to Resolution (MTTR), automates runbooks.
Each of these scenarios underscores the power of real-time, event-driven architectures. When milliseconds matter—such as fraud detection or live trading updates—webhooks provide the backbone for automated, reliable workflows.
Advanced Patterns & 2025-Style Innovations
As we look toward the cutting edge, several trends are reshaping webhoolk usage:
- Serverless Webhook Receivers
- Deploy AWS Lambda, Azure Functions, or Google Cloud Functions to auto-scale webhook handlers without managing servers.
- AI-Enhanced Event Processing
- Incorporate LLMs (e.g., GPT-4o) to classify or enrich incoming payloads—such as auto-tagging support tickets or summarizing error logs.
- Centralized Webhook Management Platforms
- Adopt services like Hookdeck or Payloadedia to visualize event streams, configure retry policies, and enforce JSON schema validation.
- GitOps-Driven Workflows
- Leverage webhooks to trigger end-to-end CI/CD pipelines: code push → automated tests → container build → deployment to production.
Long-Form Insight:
In our experience working with a global retail client, we architected a serverless webhook pipeline on AWS: incoming e-commerce events hit API Gateway, validated via AWS Lambda, then pushed into Kinesis Data Streams for real-time analytics and personalized email triggers. This design not only handled millions of events per day but also provided sub-200ms end-to-end latency, empowering the marketing team to send hyper-targeted offers within seconds of purchase.
Two In-Depth Reflections on Webhook Adoption
Integrating webhooks at scale can surface architectural challenges that aren’t obvious at first glance. Our second major client, a leading fintech firm, initially saw sporadic webhook failures due to concurrency limits on their legacy monolithic listener. By refactoring into a microservices pattern—each event type handled by its own containerized endpoint coupled with Amazon SQS dead-letter queues—they achieved near-perfect delivery rates and simplified debugging. They also implemented a real-time dashboard using Grafana and Prometheus metrics exported via custom webhoolk middl eware, giving visibility into throughput, failure rates, and average processing times. The result was a 60% reduction in support tickets related to missed events and a dramatic improvement in developer confidence.
Another case study from our SecurityOps practice highlights the importance of rigorous signature validation. A healthcare customer experienced an attempted spoofing attack where malicious actors replayed old webhook payloads to trigger unauthorized data exports. By enforcing strict HMAC checks, timestamp validation (rejecting events older than 2 minutes), and mutual TLS authentication, they locked down their webhoolk endpoints, ensuring that only genuine, timely events could drive sensitive actions. This fortified their compliance posture under HIPAA and bolstered trust among their enterprise clients.
You May Like: What Is npcap? Full Guide to Essential Network Capturing Tool
Best Practices & Common Pitfalls to Avoid
- Early Validation
- Sanitize and schema-validate payloads before any business logic. Use libraries like ajv for JSON schema enforcement.
- Immediate Persistence
- Write raw events to durable storage (e.g., Kafka, SQS, or a relational database) before processing to guarantee data recovery.
- Idempotency Keys
- Leverage unique event IDs to safely ignore duplicate deliveries—essential under at-least-once semantics.
- Asynchronous Workflows
- Decouple HTTP acknowledgment from heavy processing: respond
200 OKimmediately, then process in background jobs.
- Decouple HTTP acknowledgment from heavy processing: respond
- Back-off and Retry Logic
- If downstream services fail, implement exponential back-off with jitter to prevent thundering-herd effects.
- Versioning Contracts
- Include version identifiers in your webhoolk URLs or payloads (e.g.,
/v1/webhooks,schema_version) to avoid breaking changes.
- Include version identifiers in your webhoolk URLs or payloads (e.g.,
- Observability and Alerting
- Emit metrics for received events, processing durations, error counts, and queue backlogs. Tie into dashboards and alerts.
Conclusion Of Your Integrations Today
Webhooks empower organizations to build agile, event-driven architectures that react instantly to changing conditions—whether that’s a customer completing a purchase, a critical system alert, or a developer merging code. By embracing best practices around security, reliability, and observability, you’ll ensure your integrations remain robust as you scale.
Your Next Steps:
- Identify a manual polling process in your stack.
- Replace it with a webhoolk subscription and a simple listener.
- Instrument metrics and dashboards for end-to-end visibility.
- Share your success story with your peers!
In 2025, every millisecond counts. Let your systems speak for themselves, one event at a time—and watch your productivity and customer satisfaction soar.