Introduction to Multi-Factor Authentication
What is Multi-Factor Authentication?
Multi-Factor Authentication (MFA) is a security protocol that requires users to provide two So let’s say you have to sign in to some account or use an application, the ones which require an extra layer of security — and those are actually the most favored kinds by various people as all of us do wish to feel secure enough when doing anything for the sake of security. For that very reason, multi-factor authentication, in short MFA, exists and is applied in various secure systems. Imagine it as a padlock on your door so even if one key goes missing or is taken, it is still very difficult for one to get access.
MFA usually combines the following three types of factors:
Knowledge factors: Knowledge factors can be separated into categories of something you know, for example a password or a PIN.
Ownership factors: In this case, reference is made to something you own, which in practice is an application on your phone that provides you self destructing codes or a small physical token.
Biometric factors: This is a question of something you are, such as the opening of doors with the identification of your fingerprint or face.
These numerous security measures devised to weed out imposters from getting into various systems are hugely beneficial.
Importance of Multi-Factor Authentication
The significance of Multi-Factor Authentication is not to be neglected, notably in a time when cyber menaces have grown to be more advanced in nature. It was concluded that almost 80% of all data breaches happened because of common passwords. The outcome of this is that MFA reduces the percentage. The following is a brief summary of the factors that make this necessary:
Improved Security: The Organization’s security posture against unauthorized access is greatly enhanced with the use of MFA. In the case where the password has been compromised a verification code can be requested making it impossible for the intruder to enter.
Regulatory Compliance: GDPR and HIPAA et cetera make it mandatory for every business to put several security protocols in place. MFA ensures those in charge of organizations that their responsibilities in terms of the law are covered, hence no reason for them to be unparalleled.
Confidentiality in service: Customers are particularly happy when assured that they are in safe hands paranoia the companies they are serving. This may then serve the client’s needs in a better way.
The ongoing threat of cyber crimes demands that companies enhance their security measures and consider the adoption of Multi-factor Authentication (MFA) as standard practice within the organizations. The next sections provide opinions on different types of MFAs and their deployment.t it effectively, and the best practices for maximizing its benefits.
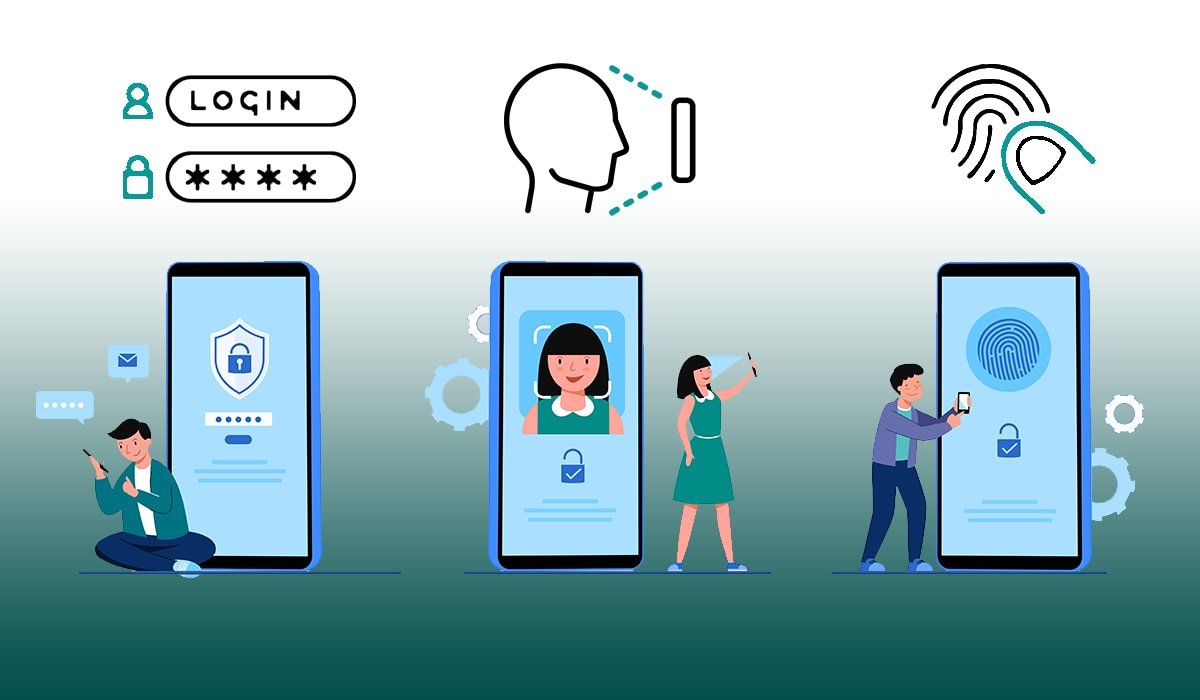
Types of Multi-Factor Authentication
Knowledge-based Factors
Before we proceed to the coverage of Multi-Factor Authentication (MFA) Types, it is very important we shed some light on how these factors can be grouped. The first class is Knowledge-based factors, which essentially cover information that is personal and therefore private to the user. It is one of the most familiar forms of authentication that a lot of people are accustomed to. Knowledge-based factors usually have:
Passwords: the most evident knowledge-based factor example. However, users are facing many challenges in creating and remembering separate passwords for various services as the internet accounts keep on growing.
PIN numbers: these are passwords that are also numeric and shorter in length. Example is the four number pin used in automated teller machines or in mobile telephones.
Security questions: questions that are required to be answered so as to verify whether the account activation was from the actual user. They may enquire for personal information for instance parents’ or siblings’ names. Much as these appear easy to use, they can also become very high risk especially when the social networks supply the thief, with the answer.
Focus may be put on the fact that possibly answering knowledge-based factors is straightforward but they are liable to social engineering and phishing attacks. Second-tier play is always a should as it can be recommended that second-tier play is achieved.ey can be vulnerable to social engineering and phishing attacks. As such, they should always be paired with another form of authentication to enhance security.
You May Like: What Cyber Insurance in 2024 – Absolutely Essential or Just Imprudent?
Possession-based Factors
Conversely, factors based on possession greatly enhance securitythe security by requiring the user to own a physical item over and above the other repetitive factors. This method is extremely reliable and harder to bypass than knowledge-based factors. Examples of these that are of the essence would include:
- Smartphone Authentication Apps: Applications like Google Authenticator and Authy generate one-time codes that users must enter in addition to their password.
- Hardware Tokens: These small devices generate temporary codes, often used in corporate settings. A common example is the RSA SecurID token.
- SMS Verification Codes: After entering a password, a code is sent to the user’s phone via text message. Although popular, this method can be susceptible to interception.
Multi-Factor Authentication (MFA) is an authentication method which requires more than one verification method from independent categories of credentials to verify the user’s identity. This type of authentication can be in the form of ‘something known,’ i.e. password, or ‘something has,’ in this case the phone or the mail. In this respect, employing both ownership and cognition factors can be used whilst combining features of the two. I will take further steps to examine the significance of these considerations within the existing traditions and will share some good ideas in reinforcing the security of MFA.
Implementing Multi-Factor Authentication
Choosing the Right Factors
In the movement towards Multi-Factor Authentication (MFA), it is quite important that different support criteria together with the MFA settings are set up for the application to work. One must be cautious not to make the management of users’ authentication unbearable at the expense of its security. This will allow for the safety measures enhancement and shall not be a burden on the application users. When implementing MFA, the following factors should be taken under consideration:
Socioeconomic characteristics: comprehend the people you are offering services or selling products to. For example, individuals who are very techy may have a preference for smartphone authentication applications which may not necessarily be the case for those with fewer technical experience, who might find using SMS verification more appropriate.
Risk Analysis: Determine the data and applications that you will be protecting whether they are low value or high value. A more secure financial services environment may necessitate the deployment of more than just these two factors – knowledge and possession factors i.e. ‘something I know’ and ‘something I have’ or the ‘two factor’ concept.
Expenses and Performed Efforts: Make a decision about the expenses and efforts to be taken to implement the factors. In certain cases, some solutions may require a sunk cost to be made with respect to equipment or the continuous necessity or expense, such as that of a hardware token.
Lastly, it is easier to craft a design in such a way that all the factors it contains fully achieve the set objective of…security but also minimizes friction for users.
Integration with Existing Systems
It is not just enough to have the right parameters, what matters is the integration of MFA into these systems. Integrating MFA into existing systems is easier said than done, but a carefully crafted plan can smoothen the process. These are some of the best approaches for seamless and efficient integration; remedial measures can be put in place to solve this issue. Some of the popular measures include this one; doing a System Audit: Look at the current systems and applications so as to identify how they can be make use of Multi-factor Authentication properly.
Finally, there are good MFA solutions out there which can integrate well within other existing platforms and are able to do so. A number of SaaS providers even have MFA features bundled in their offering such that one can activate this function with a few clicks.
Instructing and Equipping the Users: Create a training program targeting all employees for attaining new authentication processes. Remembering examples of the people who were faced with the same restriction like you could easily help understand the usefulness.
There has to be a prior check and the system has to be improved once launched – test and ask some users to try it before implementing MFA to rule out possible defects and need for corrections.
After selecting the criteria and including them in the operational mechanism, the organizations will be focused on improvement of information security within [ost organizations internal policies increase confidence and trust of customers. Best practices in the next section.s to ensure the effective use of Multi-Factor Authentication.

Best Practices for Multi-Factor Authentication
Regularly Update Authentication Methods
As organizations continue to harness the power of Multi-Factor Authentication (MFA), it’s essential to commit to regular updates of authentication methods. In today’s rapidly evolving cybersecurity landscape, outdated methods can become vulnerable, exposing sensitive information to potential breaches. Consider these best practices for keeping authentication methods fresh:
- Assess Risk Regularly: Conduct routine evaluations to identify new threats and weaknesses in existing authentication processes. This will help you stay ahead of cybercriminal tactics.
- Technology Advancements: Keep an eye on the latest authentication technologies. Biometric methods, like facial recognition or fingerprint scanning, are continuously improving and can add an additional layer of security.
- User Feedback: Encourage users to provide feedback about their experiences with MFA tools. If a particular method becomes cumbersome or is met with resistance, it might be time to explore alternatives.
Regular updates not only enhance security but also demonstrate a proactive commitment to protecting user data.
User Education and Training
Equally important to having robust MFA systems in place is ensuring that users are well-educated and trained on the importance and operation of these systems. Many vulnerabilities arise from user errors, making education a key element in a successful MFA strategy. Here are ways to foster an understanding of MFA among users:
- Comprehensive Training Sessions: Organize initial training sessions that explain MFA concepts, the reasons for its implementation, and a walkthrough of how to use different authentication methods effectively.
- Create Informative Resources: Consider developing manuals, FAQs, or visual guides that users can reference. Visual aids, such as flowcharts, can clarify the steps involved in the authentication process.
- Share Real-World Examples: Use stories (potentially anonymized) of phishing attempts or data breaches to emphasize the importance of using MFA. Hearing about genuine situations can resonate more deeply and motivate compliance.
Educated users are your first line of defense against cyber threats. By investing in user education and keeping authentication methods up to date, organizations can build a resilient security culture that adapts to emerging risks. In the subsequent sections, we will explore the substantial security benefits provided by Multi-Factor Authentication, including its role in protecting against phishing attacks and preventing unauthorized access.

Security Benefits of Multi-Factor Authentication
Protection Against Phishing Attacks
One of the most significant security benefits of Multi-Factor Authentication (MFA) is its ability to protect against phishing attacks. Phishing is a prevalent method used by cybercriminals to deceive users into disclosing personal information, such as usernames and passwords. These attacks can occur via email, texts, or even through fake websites that mimic legitimate ones. MFA acts as a robust line of defense in the following ways:
- Added Layer of Security: Even if a user falls victim to a phishing scam and unknowingly provides their password, the attacker won’t have access to the second authentication factor, whether it’s a text message code or an authentication app’s generated code. This dramatically reduces the likelihood of account takeover.
- Real-Time Alerts: Many MFA systems provide alerts for logins attempted from unfamiliar devices or locations. Users can quickly identify suspicious activities, enabling them to take the necessary precautions, such as changing passwords immediately.
For instance, there’s a story of a colleague who almost fell for a phishing email from what appeared to be their bank. Although they unwittingly shared their password, the additional layer of MFA sent a code to their phone. Because they hadn’t requested a login, they realized something was amiss and avoided what could have been a costly mistake.
You May Like: How to Remove Personal Information from Google Search
Prevention of Unauthorized Access
Another essential advantage of MFA is its effectiveness in preventing unauthorized access. In today’s digital landscape, protecting sensitive data from unauthorized entities is of utmost importance—regardless of the industry. Here’s how MFA ensures that only authorized users gain access:
- Dual Verification Requirements: By requiring multiple forms of identification, MFA creates significant barriers for unauthorized users who only possess a password. This dual verification makes it challenging for hackers to gain unauthorized access, even with a compromised password.
- Limitations on automated attacks: Automated attacks rely on the ability to rapidly test stolen credentials. With MFA in place, attackers encounter roadblocks in their attempts to infiltrate accounts, buying organizations crucial time to detect and respond to threats.
For example, when a financial institution implemented MFA, they reported a 90% drop in unauthorized access attempts within just a couple of months. This speaks volumes about the potential impact of a robust MFA framework. In summary, Multi-Factor Authentication not only guards against phishing attacks but also significantly decreases the risk of unauthorized access. As we continue our journey, we will examine the regulatory and compliance aspects associated with MFA and discuss how staying compliant is crucial for organizations.
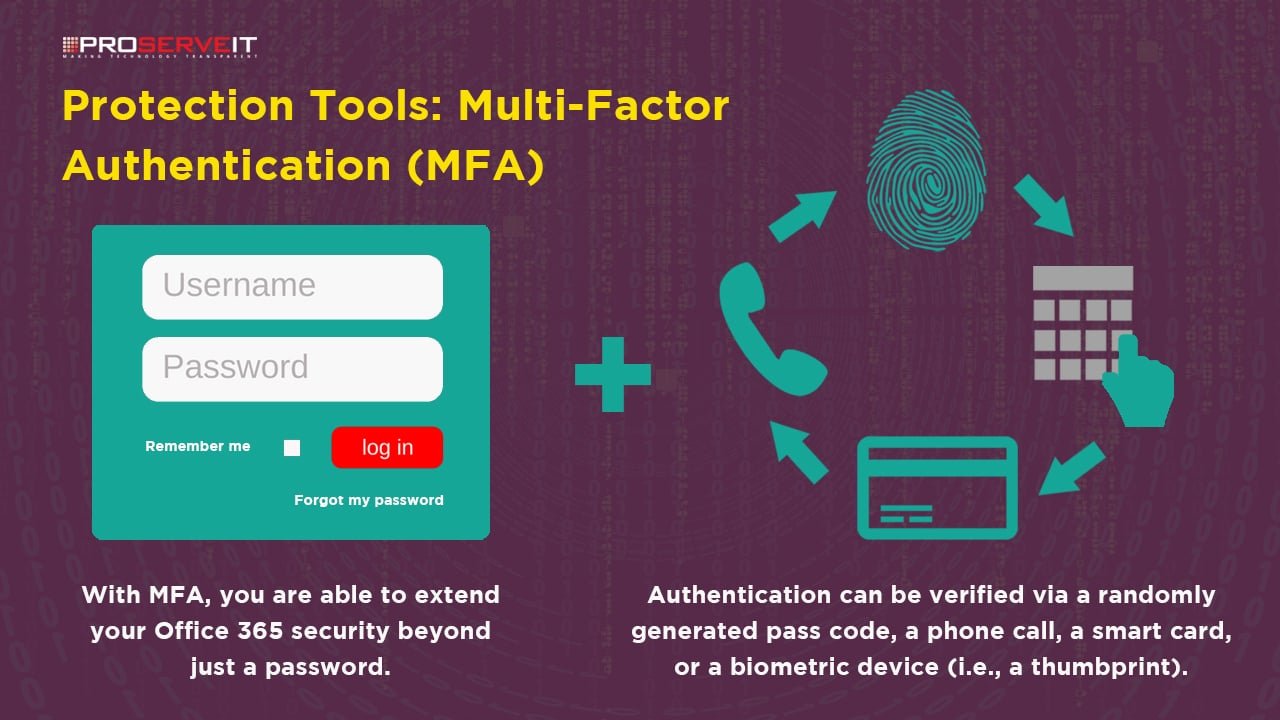
Regulations and Compliance
Compliance Requirements
As organizations increasingly adopt Multi-Factor Authentication (MFA), understanding the associated compliance requirements becomes crucial. Regulatory bodies across various industries often mandate specific security protocols to safeguard sensitive data. Compliance with these regulations isn’t just a best practice; it’s often a legal obligation. Many industries face stringent compliance standards, including:
- Financial Services: Regulations such as the Gramm-Leach-Bliley Act (GLBA) require financial institutions to implement robust security measures, including MFA, to protect consumer information.
- Healthcare: The Health Insurance Portability and Accountability Act (HIPAA) mandates that healthcare providers secure patient data, making MFA a vital component in their security frameworks.
- Payment Card Industry: The Payment Card Industry Data Security Standard (PCI DSS) explicitly states that MFA must be implemented for access to sensitive information.
Following compliance requirements not only helps organizations avoid hefty fines but also enhances their overall security posture. For example, one organization in the healthcare sector implemented MFA to comply with HIPAA regulations. Not only did they avoid potential fines, but they also reported improved patient trust and satisfaction.
Data Protection Regulations
In addition to industry-specific compliance requirements, data protection regulations also shape how organizations implement MFA. These regulations often emphasize the need for strong security measures to protect user data from breaches. Key data protection regulations include:
- General Data Protection Regulation (GDPR): For organizations operating within the European Union or handling EU citizens’ data, GDPR mandates strong security practices, making MFA a recommended measure for data safeguarding.
- California Consumer Privacy Act (CCPA): This regulation requires companies collecting personal information to implement reasonable security procedures. MFA aligns perfectly with these expectations, providing a safeguard against unauthorized access.
Adhering to these data protection regulations not only mitigates risks related to data breaches but also boosts an organization’s credibility. For instance, an e-commerce business that adopted MFA after the introduction of CCPA saw a marked increase in consumer confidence. Customers felt assured their data was secure, leading to a rise in sales. In conclusion, understanding and adhering to compliance requirements and data protection regulations through the implementation of Multi-Factor Authentication can significantly enhance an organization’s security infrastructure. As we delve deeper into challenges and solutions associated with MFA, we’ll discover how to tackle common obstacles effectively.

Challenges and Solutions
User Experience Challenges
While Multi-Factor Authentication (MFA) plays a critical role in strengthening security, it’s essential to recognize the user experience challenges that can arise during its implementation. Many users find MFA to be cumbersome, which can lead to frustration and even resistance against using it. Some common user experience challenges include:
- Increased Complexity: The addition of multiple authentication steps can make logging in feel like a chore. Users accustomed to quickly accessing their accounts may find extended login processes irksome.
- Difficulty with Authentication Methods: Not all users are comfortable with technology, and some may struggle with specific authentication methods, like using an authentication app or understanding SMS verification.
- Lockout Issues: Users can sometimes find themselves locked out of their accounts if they don’t have access to their second factor or misplace their authentication device. This can induce stress and feelings of helplessness.
For example, a friend of mine shared a frustrating experience where he couldn’t access his banking app due to a lost phone. The couple of hours spent recovering his account felt like an eternity, and he almost considered switching to a competitor with a simpler login process.
Solutions to Enhance User Experience
To maintain security without sacrificing user experience, numerous strategies are available to make MFA implementation easier. These strategies include – Oversight over MFA technology adoption to ensure that the MFA technologies used are easy to adopt and actually help in catering to the specific group of end-users. Moreover, engaging in studies helps in understanding the type of MFA that the majority of the users would rather be subjected to.
Flexibility In Authentication: With this factor, there exist options of presenting more than one factor in the challenge. This is where some people may like the application method, whereas other people would rather prefer the SMS-based solution or even a hardware-based token.
SSO allows for a more efficient process considering users logging in multiple times in high frequency intervals. It makes sure that users are able to access data from several systems by entering single set of MFA data.
Corrective Measures And Assistance: Provision of a step by step instructions on how one can install any form of MFA and its usage together with the possibility of video tutorials and FAQs is always good. Additionally, implementing a customer powerful enough to aid the user when they encounter any trouble is essential.
Organization helps bolster good feelings towards MFA by actively mitigating any efficiency-cum-implementation incongruities. Once the chapter is investigated further, the lessons learned during the different MFA operations will be appreciable.

Case Studies: Successful MFA Implementations
Enterprise MFA Deployment
As organizations continue to prioritize security, enterprises are turning to Multi-Factor Authentication (MFA) as a critical component of their cybersecurity strategies. One notable case is that of a large financial services firm that found itself targeted by increasing cyber threats. To bolster its defenses, the firm implemented MFA across all employee accounts, which included access to sensitive customer data and internal systems. Here are key aspects of their deployment:
- Method Variety: The organization employed a combination of authentication methods—like biometric scans for high-level access and hardware tokens for regular employees—to strike a balance between security and user convenience.
- Training Programs: Recognizing that security is only as strong as its users, the firm launched extensive training programs to educate employees about MFA benefits and proper usage.
- Immediate Impact: Within just a few months, the firm reported a 75% decrease in unauthorized access attempts. This significant drop reinforced employee confidence in utilizing MFA as a daily practice.
This enterprise case illustrates that large organizations reaping the benefits of MFA can produce tangible results with strategic planning and user engagement.
You May Like: Why Cybersecurity is Non-Negotiable for the Safety of Autonomous Vehicles 2024
Small Business MFA Implementation
While large enterprises are often highlighted in case studies, small businesses also have Use a case study or recount an anecdotal scenario on MFA as evidence would be necessary to prove the weakness of the opposition or the strength of the proponents of the policy. For instance, there is a local digital marketing firm that was attacked because it used weak passwords. Being the problem solvers they are, the business decided to install MFA into all its processes.
That’s why they just did it the easy way: within two birds with one stone, multiple, technologically only sane and hence secure, SMS-based solutions were among their culprits with email codes often present. That is, there were quite a number of nontechnical employees who would need MFA, but the comprehensive documentation made them all empowered in terms of its operation.
Conned every other aspect of their HR policy, the firm decided to speak individual languages or have a video conference because remote support is the new ‘in-thing’. During this meeting, it was made clear that the expectation was that all employees irrespective of their age or official designation present in those offices will adopt MFA.
The last line of this short story will help readers observe another reality about the appropriate use of MFA – the implementation of such a security and risk management control measure is not the preserve of big-worded organizations only. Unlike more costly and complex administrative controls where some security measures may be out of reach for smaller organizations, appropriately tailored measures can be developed wherever. In conclusion, it is beyond argument that Multi-Factor Authentication offers a significant scope in cyberdefense across different industries. Anticipating the impending progress in MFA, next we would have a closer look at biosystems and AI-backed systems.