Introduction
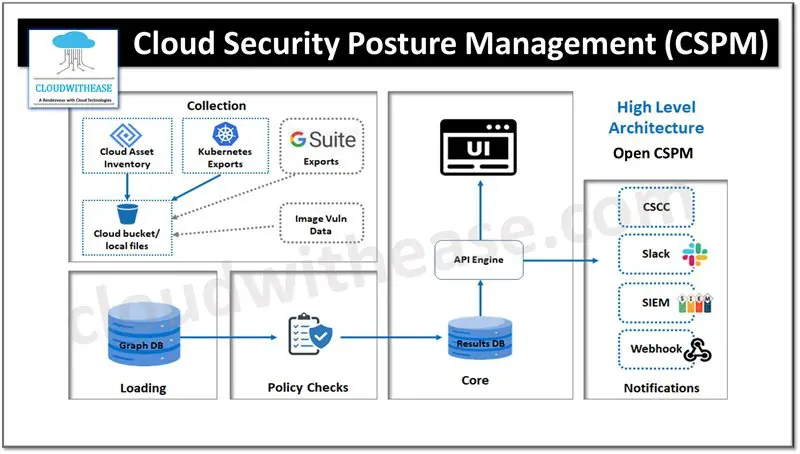
Overview of Cloud Security Posture Management (CSPM)
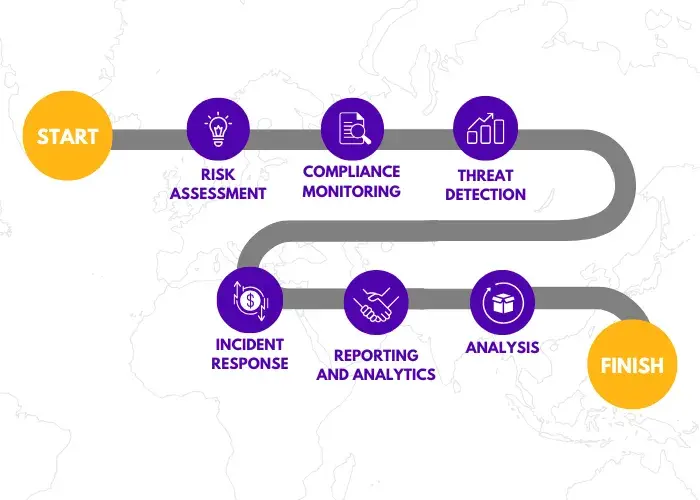
In today’s digital age, organizations are increasingly migrating their operations to the cloud to enhance scalability, efficiency, and collaboration. However, with this shift comes the paramount need to protect cloud environments from security threats. This is where Cloud Security Posture Management (CSPM) comes into play. CSPM is a suite of tools and practices designed to identify, manage, and remediate potential security risks in cloud-native infrastructure. These tools help organizations maintain compliance with industry standards and improve their overall security posture by continuously assessing their environments. Key features of CSPM include:
- Risk Assessment: Evaluating potential vulnerabilities in cloud configurations.
- Policy Compliance: Ensuring adherence to regulatory requirements.
- Real-time Monitoring: Identifying misconfigurations and threats as they occur.
This multi-faceted approach not only identifies risks but also recommends remediation actions, offering organizations a comprehensive way to protect their assets.
| Components | Description | Examples |
| Configuration Management | Monitors and evaluates cloud resources to ensure configurations align with security best practices. | Checking for public access on storage buckets, ensuring encryption on databases. |
| Risk Assessment | Identifies and prioritizes security risks across cloud resources. | Identifying unencrypted data, unused permissions, misconfigured security groups. |
| Compliance Monitoring | Ensures adherence to regulatory and internal compliance standards. | Compliance checks for standards like GDPR, HIPAA, PCI DSS, and SOC 2. |
| Threat Detection | Monitors for potential security threats and suspicious activity in cloud environments. | Detecting unauthorized access, suspicious logins, and anomalous API activity. |
| Remediation and Automation | Automates responses to resolve security issues and misconfigurations. | Auto-remediation for policy violations, like revoking overly permissive access. |
| Visibility and Reporting | Provides centralized visibility and reporting on cloud security posture across environments. | Dashboards for compliance scores, audit trails, and posture assessments. |
| Alerting and Notifications | Sends alerts for high-risk issues to appropriate stakeholders. | Notifications for newly detected vulnerabilities or changes in resource configurations. |
Importance of Protecting Cloud Infrastructure
With the rapid adoption of cloud technologies, safeguarding cloud infrastructure is more critical than ever. An unexpected security breach can have devastating effects, leading to financial loss, reputational damage, and regulatory penalties. Imagine a mid-sized tech company that decides to store sensitive customer data in the cloud. Without robust cloud security posture management, they could unknowingly expose this data to unauthorized users, leading to a massive data breach. The fallout could include:
- Financial Costs: Legal fees, fines, and loss of customer trust can quickly escalate.
- Reputation Damage: Customers may hesitate to do business with a company known for security oversights.
- Operational Disruption: A data breach could result in downtime, affecting productivity and service delivery.
Protecting cloud infrastructure is not just an IT challenge; it’s a critical business imperative. By employing CSPM strategies and tools, organizations can proactively address vulnerabilities, ensuring their cloud environments remain secure and resilient against evolving threats. In conclusion, understanding the role of CSPM and the necessity of cloud security is essential for safeguarding an organization’s assets in an increasingly cloud-centric world.
Evolution of CSPM
Historical Perspective
To understand where Cloud Security Posture Management (CSPM) is today, it’s vital to look back at its origins. The transition to cloud computing began in earnest in the early 2000s, where organizations recognized the benefits of flexible, on-demand infrastructure. However, as more businesses adopted cloud services, they encountered a significant hurdle: security. In the beginning, most security measures relied on traditional network security frameworks. Firewalls and intrusion detection systems were prevalent, but they failed to address the unique challenges posed by cloud environments. This led to the emergence of CSPM as a unique category of security management. Key milestones in CSPM evolution include:
- 2010s: The rise of multi-cloud strategies prompted the need for tools that could provide visibility and control across various platforms.
- Introduction of Automation: Organizations began integrating automated tools to enhance security monitoring and compliance checks.
- Mainstream Adoption: By the mid-2010s, recognizing the potential risks of cloud misconfigurations prompted companies to implement CSPM solutions more widely.
This historical perspective highlights how CSPM evolved from basic security protocols to an essential tool for modern organizations navigating complex cloud landscapes.
Current Trends in CSPM
Fast forward to today, and CSPM has adapted to meet the pressing security demands of increasingly sophisticated threats. Here are some current trends shaping the CSPM landscape:
- Integration with DevOps: As organizations embrace DevOps methodologies, CSPM solutions are integrating seamlessly into development pipelines to ensure security from the start.
- AI and Machine Learning Adoption: Many CSPM tools now harness the power of artificial intelligence to predict and mitigate risks automatically. This enhances threat detection by analyzing patterns and anomalies more efficiently than traditional methods.
- Focus on Compliance: With regulations like GDPR and HIPAA getting stricter, CSPM tools now include compliance monitoring features, helping organizations to stay ahead of regulatory requirements.
- Emphasis on Visibility: Organizations demand real-time insights into their cloud environments. Modern CSPM solutions provide dashboards that offer comprehensive visibility into potential vulnerabilities and compliance issues.
The evolution of CSPM from its humble beginnings to the advanced, integrated solutions available today underscores its importance in securing cloud infrastructure. As threats continue to emerge, staying updated on the latest trends in CSPM will be crucial for organizations looking to enhance their security posture.
You May Like: Say Goodbye to Passwords Biometrics Is Here: The Evolution of Biometrics in Security 2024
Understanding Cloud Infrastructure Threats
Common Cloud Security Risks
As organizations increasingly depend on cloud infrastructure, understanding the common security risks associated with this shift is essential for safeguarding data. Many businesses mistakenly believe that moving to the cloud automatically ensures security, but that’s far from the truth. Here are some prevalent cloud security risks to be aware of:
- Misconfigurations: One of the most frequently encountered threats, misconfigurations can lead to exposure of sensitive data. In many cases, settings are accidentally left open, allowing unauthorized access.
- Data Breaches: Weak credentials and inadequate access controls can open the door for cybercriminals to exploit vulnerabilities. A lack of encryption can exacerbate this issue, leaving data in transit or at rest susceptible to interception.
- Insider Threats: Not all threats come from outside the organization. Employees with access to sensitive data can unintentionally or maliciously expose information, leading to significant security breaches.
- Account Hijacking: Cybercriminals use phishing techniques to deceive employees into revealing their credentials, allowing attackers entrée into the cloud infrastructure.
Understanding these risks is the first step in implementing effective CSPM strategies to protect against them.
Impact of Data Breaches on Cloud Environments
The ramifications of a data breach can be profound, affecting not only an organization’s financial health but also its reputation. Consider the story of a healthcare provider that stored millions of patient records in the cloud. When a data breach occurred due to insufficient security measures, the fallout was immediate and severe:
- Financial Costs: The organization faced hefty fines amounting to millions of dollars, not to mention legal fees and the costs associated with remediation efforts.
- Reputation Damage: Trust is crucial in the healthcare sector. Patients began to question the provider’s ability to protect their personal health information, leading to a decline in business.
- Operational Disruption: The breach resulted in significant downtime as the company worked to restore security and confidence, affecting patient care and service delivery during that period.
Data breaches can also lead to long-term consequences, such as increased scrutiny from regulators and higher insurance premiums. Therefore, organizations need to prioritize cloud security by leveraging CSPM solutions to mitigate these risks proactively. Ensuring appropriate protocols and configurations are in place can help fortify cloud environments against potential breaches.

Benefits of Implementing CSPM Solutions
Enhanced Visibility and Control
One of the standout benefits of implementing Cloud Security Posture Management (CSPM) solutions is the enhanced visibility and control they provide. In the complex and often fragmented world of cloud infrastructure, it can be challenging to maintain an awareness of what’s happening across your environment. Imagine a scenario where an organization uses multiple cloud providers. Without CSPM, the likelihood of misconfigurations or oversights—like unwanted open ports—is considerably higher. CSPM solutions change that by offering a centralized view of the cloud environment, allowing organizations to:
- Identify Misconfigurations: CSPM tools automatically scan configurations to spot vulnerabilities and provide actionable insights to correct them.
- Monitor Changes in Real Time: This feature enables organizations to detect unauthorized changes, ensuring that any security threats are addressed immediately.
- Visualize Security Posture: Dashboards can present comprehensive metrics on compliance, vulnerabilities, and risk levels across multiple cloud platforms, enabling informed decision-making.
With improved visibility, organizations can take immediate action to mitigate risks, improving overall security and compliance posture.
Automation of Compliance Monitoring
As regulations surrounding data protection become more stringent, the need for effective compliance monitoring has never been more apparent. CSPM solutions address this challenge through automation, streamlining the compliance process significantly. Here are a few ways automation transforms compliance monitoring:
- Continuous Compliance Checks: CSPM tools provide continuous monitoring against compliance frameworks such as GDPR, HIPAA, and PCI-DSS. They automatically assess configurations and rectify any non-compliance issues.
- Audit Readiness: With automated logging and reporting features, preparing for audits becomes less stressful. Organizations can easily access documentation that demonstrates compliance, allowing for a more efficient, streamlined audit process.
- Reduced Manual Effort: Automating compliance processes minimizes the risk of human error. This not only saves time but also frees up valuable resources that can be redirected to other areas of security management.
For instance, a financial institution utilizing CSPM might find that automated compliance checks reduce their manual oversight time by over 60%. This efficiency not only ensures adherence to regulations but also enhances the organization’s overall security posture. In conclusion, the enhanced visibility and control combined with automated compliance monitoring fundamentally equips organizations to navigate the complexities of cloud security. By embracing CSPM solutions, businesses can fortify their defenses against threats while remaining compliant with evolving regulations.
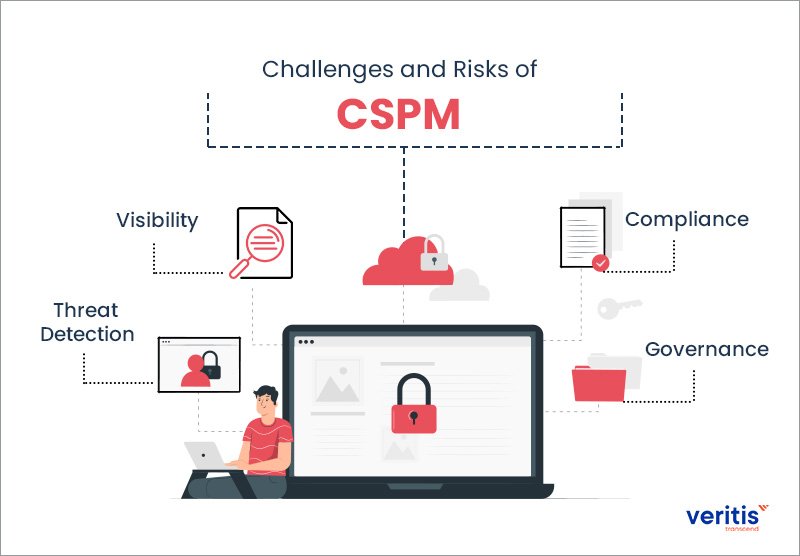
Key Features of a Robust CSPM Platform
Real-time Threat Detection
As businesses continue to migrate their operations to the cloud, ensuring security becomes paramount. One of the key features of a robust Cloud Security Posture Management (CSPM) platform is real-time threat detection. In today’s rapidly evolving threat landscape, the ability to detect security issues as they emerge can make all the difference in mitigating damage. Real-time threat detection offers several benefits, including:
- Immediate Alerts: CSPM solutions continuously monitor cloud configurations for any signs of unusual activities or vulnerabilities. When a threat is detected—such as unauthorized access attempts or misconfigurations—alerts are sent out immediately, enabling swift remediation.
- Behavioral Analytics: Many CSPM tools leverage machine learning to establish a baseline of normal activities. When deviations occur, it triggers alerts in real-time, allowing teams to respond proactively rather than reactively.
- Integration with Security Operations: By integrating with existing security systems, CSPM platforms enhance an organization’s overall security strategy. For example, an organization could configure its CSPM to work in tandem with a Security Information and Event Management (SIEM) system, streamlining the response process.
Imagine an online retail company that experienced a surge in unauthorized access attempts during a peak shopping season. With a CSPM platform in place, the security team was alerted immediately, allowing them to implement access controls before customer data could be compromised.
You May Like: Why Cybersecurity is Non-Negotiable for the Safety of Autonomous Vehicles 2024
Policy Configuration and Enforcement
Another critical feature of a robust CSPM platform is effective policy configuration and enforcement. As organizations expand their cloud landscapes, establishing consistent security policies becomes increasingly challenging. CSPM platforms help simplify this process in several ways:
- Customizable Policy Frameworks: Organizations can define tailored security policies that align with their specific compliance requirements and risk tolerance. This allows for a one-size-fits-all approach to security that is often ineffective.
- Automated Policy Enforcement: Once policies are set, CSPM tools ensure that they are enforced continuously across cloud environments. If a policy violation occurs—such as an open security group—automated responses can remediate the issue instantly.
- Centralized Management: A centralized dashboard enables security teams to view compliance status and allow for efficient policy management across different cloud providers.
For instance, an energy company may implement strict data privacy policies due to regulatory requirements. With a CSPM solution, these policies can be enforced automatically, ensuring that appropriate security measures are in place and that any deviations are addressed swiftly. In summary, real-time threat detection coupled with stringent policy configuration and enforcement are vital features of a robust CSPM platform. Together, they create a proactive security environment that not only defends against threats but also fosters compliance with evolving regulatory requirements, empowering organizations to focus on their core operations with confidence.

Best Practices for Securing Cloud Infrastructure
Implementing Multi-factor Authentication
As organizations navigate the complexities of cloud infrastructure, adopting best practices for security becomes crucial. One highly effective method is implementing multi-factor authentication (MFA). By requiring users to provide two or more verification factors before gaining access, MFA adds an extra layer of protection that makes it significantly harder for unauthorized individuals to breach accounts. Consider this: if a cybercriminal compromises a password, MFA can thwart potential intrusions by demanding another verification step. Here’s how MFA enhances security:
- Layered Security: By requiring something the user knows (like a password) and something they have (like a mobile device for a one-time code), MFA creates multiple barriers against unauthorized access.
- User Education: Implementation of MFA also provides an opportunity to educate users about the importance of cybersecurity, fostering a culture of awareness within the organization.
- Reducing Credential Theft Risks: With phishing attacks on the rise, MFA acts as a safeguard. If a user falls victim to a phishing attack but has MFA enabled, the attacker cannot easily access their account without the additional verification.
For example, an IT manager at an e-commerce startup decided to implement MFA after a colleague’s account was compromised through a phishing attack. The swift adoption of MFA not only protected sensitive customer data but also instilled confidence among customers about their information safety.
Regular Security Audits and Assessments
Another critical best practice is conducting regular security audits and assessments. The cloud landscape is not static; it continuously evolves as organizations introduce new applications and users. Regular audits ensure that security measures are up-to-date and effective. Here are some key components of effective security audits:
- Comprehensive Reviews: Security audits should evaluate all aspects of cloud infrastructure, including user access logs, data encryption standards, and compliance with regulatory frameworks.
- Identifying Vulnerabilities: Regular assessments help organizations stay ahead of potential threats by identifying vulnerabilities before attackers can exploit them. This proactive approach can prevent data breaches and other security incidents.
- Action Plans for Compliance: Security audits not only help in identifying security gaps but also provide frameworks for creating action plans to address non-compliance with industry regulations.
A healthcare organization, for instance, performed quarterly security assessments to meet stringent HIPAA regulations. During one audit, they discovered outdated encryption protocols that could have put patient data at risk. By acting on these insights, they were able to resolve the issue before any harm occurred. In conclusion, implementing multi-factor authentication and conducting regular security audits are essential practices in securing cloud infrastructure. By adopting these strategies, organizations can significantly reduce the risk of data breaches, while also promoting a culture of security awareness that empowers all users in maintaining robust protections against evolving threats.
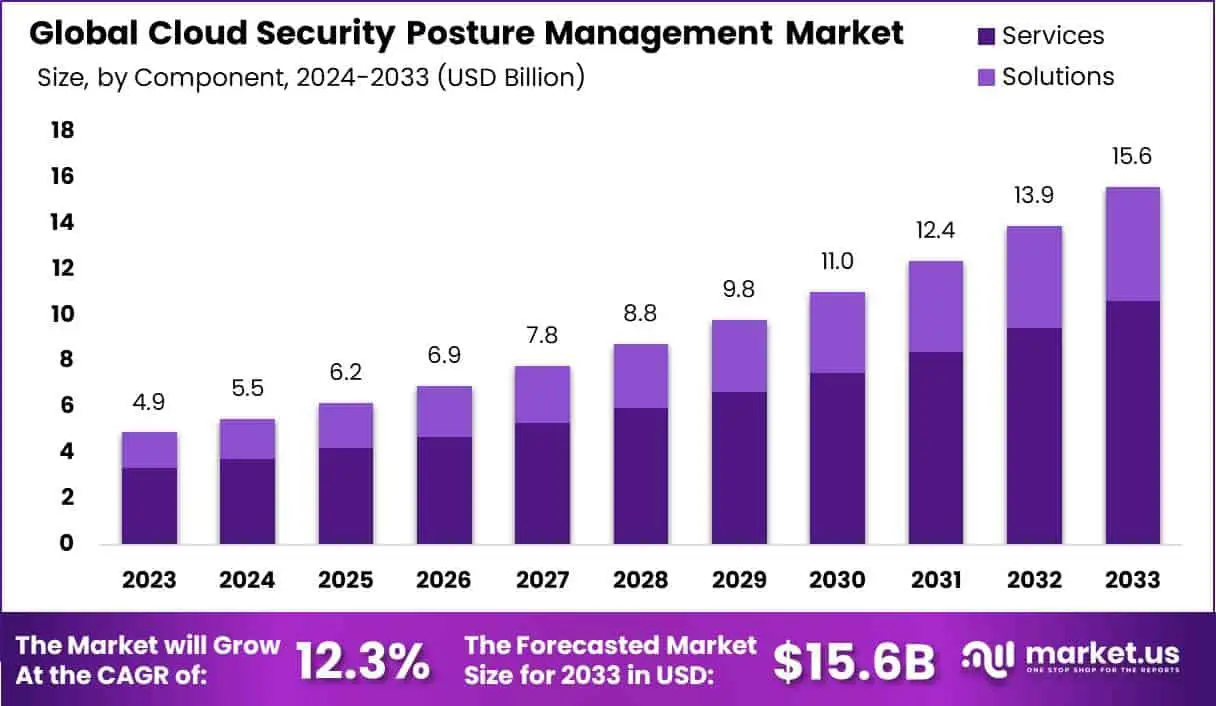
Future Outlook for CSPM Technologies
Emerging Trends in Cloud Security
As businesses continue to expand their reliance on cloud technologies, the landscape of cloud security is evolving rapidly. One of the most significant trends is the enhancement of Cloud Security Posture Management (CSPM) through advanced technologies that aim to bolster security measures proactively. Here’s a closer look at some emerging trends shaping the future of CSPM:
- Artificial Intelligence and Machine Learning: CSPM solutions are increasingly adopting AI and machine learning capabilities to analyze data patterns and detect anomalies effectively. This not only speeds up threat detection times but also reduces false positives, allowing security teams to focus on genuine threats.
- Shift Left Approach: Integrating security earlier in the development process—known as the “Shift Left” approach—is gaining traction. By embedding security in the DevOps pipeline, organizations can mitigate risks right from the coding stage, reducing potential vulnerabilities before they reach production.
- Zero Trust Security Model: The Zero Trust paradigm, which operates on the principle of “never trust, always verify,” is becoming a standard in cloud security. CSPM tools will increasingly adopt this model to assess trust at every access request, enhancing data protection further.
For instance, a fintech startup managing sensitive financial data adopted AI-driven CSPM tools to enhance real-time threat detection. This proactive security stance not only improved their security posture but also provided peace of mind to customers regarding their data safety.
You May Like: 2024’s Ultimate Guide to Multi-Factor Authentication Best Practices
Forecast for the Adoption of CSPM Solutions
The forecast for CSPM solution adoption is decidedly optimistic. According to industry reports, the global CSPM market is expected to grow significantly over the next few years, driven by evolving security demands and increased regulatory scrutiny across various sectors. Here are some key factors contributing to this growing adoption:
- Increased Regulatory Compliance: As organizations face more stringent compliance requirements, CSPM tools will become essential for maintaining adherence to regulations such as GDPR, HIPAA, and PCI-DSS.
- Multi-cloud Strategies: The shift towards multi-cloud environments means organizations will increasingly need tools that provide visibility and control across different cloud platforms, bolstering demand for CSPM solutions.
- Rising Cybersecurity Threats: With cyber threats on the rise, the urgency for businesses to safeguard their data and infrastructure will drive the adoption of advanced CSPM tools tailored to meet these challenges.
For example, a healthcare provider, facing new HIPAA regulations, decided to adopt a CSPM solution to ensure compliance and streamline security monitoring. The organization reported a remarkable reduction in security incidents and notable improvements in their compliance audits. In conclusion, as the landscape of cloud security continues to evolve, the demand for CSPM technologies is projected to grow significantly. By keeping pace with emerging trends and integrating CSPM into their security strategies, organizations can fortify their cloud environments and safeguard sensitive data against an ever-changing array of threats.
Case Studies of Successful CSPM Implementations
Industry-specific Use Cases
Cloud Security Posture Management (CSPM) has proven its value across various sectors by providing tailored solutions that meet unique industry needs. Let’s explore some industry-specific use cases that highlight the effectiveness of CSPM implementations.
- Healthcare Sector: In a prominent healthcare organization dealing with patient data, implementing a CSPM solution helped ensure compliance with HIPAA regulations. By continuously monitoring configurations and identifying vulnerabilities in their cloud infrastructure, the organization reduced the risk of data breaches significantly. As a result, the organization reported a 40% decrease in compliance-related incidents within the first year.
- Financial Services: A leading bank adopted a CSPM tool to manage its multi-cloud strategy effectively. By automating risk assessments and compliance checks across different cloud environments, they not only streamlined security operations but also improved their response to audits. The bank experienced a remarkable reduction in audit preparation time by over 50%, enabling their teams to focus on strategic initiatives rather than compliance maintenance.
- Retail Sector: In the retail industry, a large e-commerce company faced increasing challenges related to security threats and misconfigurations. By implementing a CSPM solution, the company gained real-time insights into their cloud configurations. Over six months, they addressed 95% of identified misconfigurations, resulting in enhanced data security and improved customer trust.
These examples demonstrate how CSPM can be tailored to address specific challenges across various industries, driving significant improvements in security posture and compliance. You can find many examples of companies here: https://www.gartner.com/reviews/market/data-security-posture-management.
Performance Metrics and ROI Analysis
To understand the success of CSPM implementations, organizations must measure performance metrics and analyze return on investment (ROI). Key performance metrics typically include:
- Reduction in Security Incidents: Organizations should track the number of security incidents before and after CSPM implementation. A significant decrease indicates improved security posture.
- Time Savings on Compliance: Analyzing how much time is saved on compliance-related tasks can be revealing. CSPM tools often streamline these processes, directly impacting labor costs.
- Cost of Breaches: Organizations can quantify the potential cost of security breaches and compare it to the investment in CSPM solutions. Lowering the risk of breaches can yield substantial financial savings.
Using a hypothetical example, let’s say a medium-sized company invests $50,000 in a CSPM solution. Over the first year, they reduce security incidents by 80%, resulting in a savings of $200,000 from avoided breaches and compliance fines. Additionally, they cut down compliance preparation time by 60%, translating to a further $30,000 in savings. This brings their total potential savings to $230,000 against an initial investment of $50,000—a clear ROI of 460%. In summary, successful CSPM implementations showcase transformative benefits across various industries. By leveraging specific use cases and clearly measuring performance metrics, organizations can better appreciate the value of CSPM and its impact on security, compliance, and overall ROI.