Introduction
Overview of Sonar Software
In the days we are living in, the world has become more technologically advanced and so no longer do people sensibly aspire to have network protection, it is a must. Recently, cutting edge technologies getting applied in enterprises has raised the centrality of concern. It is network protection that is applicable; for example, to seek cyber threats and with organizations benefiting more the last few years. In every corner of the IT sector, one can believe and support the recent fears about security, but space isn’t all there. For example, many of us rely on firewalls which cannot prevent exploitation of systems. It is in this regard that organizes supply chains where violation of various sorts leverages the system.-entry restriction to only the corporation’s information on the internet and excluding Sonar is yet another case of retrieving applicative exploitation of security.
- Automated Scanning: Saves time and resources while ensuring no area is overlooked.
- User-Friendly Interface: Enables easy navigation, even for those without a deep technical background.
- Reporting Tools: Offers detailed reports that help stakeholders understand vulnerabilities and prioritize resolutions.
Importance of Real-Time Vulnerability Detection
The need to be able to detect threats right away is no longer a want but a must within any establishment. That global cyber-attack targeting many companies might happen any time. Such compromises frequently result in a lot of negative consequences including but not limited to losses that are financial in nature or degradation of reputation or legal issues. Such actions are very impactful when it comes to the use of Sonar capabilities. Why is it so important to configure it in real-time mode?
Called Action: This is because the vulnerabilities are fixed and remediated the quicker they are discovered.
Vulnerability Impact: Timely warnings can help meaningfully decrease possible vulnerability exploitation.
Forwarded Defense: This then allows engaged entities to partake of, and evolve their security remedies as per the attack trends.
This also must pay more particularly under the auspices of any software provider, Sonar Software. Let’s start with risks such as adequate protection against attacks or, on the contrary, works producing a certain organization in a beneficial manner. How do we create a new rather than a protective culture on security – “pro security” ? tool is an investment in safeguarding valuable digital assets and ensuring peace of mind in an increasingly uncertain cyber landscape.
You May Like: What Is Endpoint Detection and Response – EDR Security
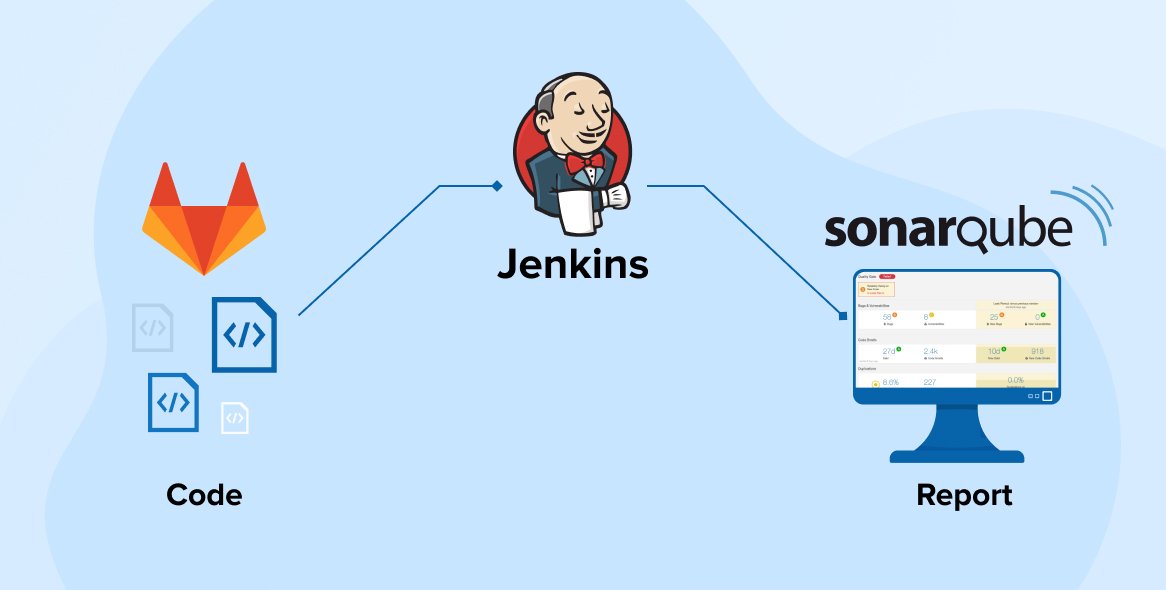
How Sonar Software Works
Scanning Mechanism
Acknowledging the importance of real-time vulnerability detection, it is essential to apprehend the modus operandi of the Sonar Software Platform. A more technical connotation branded (as of recent by some users) sums it up as the advanced vulnerability scanning engine of Sonar. The analysed vulnerabilities were the result of the ‘magic’ being done at this stage. Sonar uses advanced scanning intensity to identify security vulnerabilities of target network. This is how it operates:
- Network Mapping: Sonar first maps the entire network architecture, identifying all connected devices. This includes servers, workstations, and IoT devices, ensuring nothing is left unchecked.
- Vulnerability Identification: Using a vast database of known vulnerabilities, Sonar compares each device against these records, meticulously checking for weaknesses and misconfigurations.
- Customizable Scanning: Users can configure scans tailored to their specific needs, scheduling scans during off-peak hours to minimize impact on daily operations.
In my experience, deploying regular scans helped uncover overlooked security gaps that could have led to substantial risks.
You May Like: Understanding the Differences Between Data Warehouses and Big Data Systems
Data Analysis Process
The process of studying the scanning results comprises the fundamental part of the data analysis process – this is where Sonar takes all the unstructured information from the scanning process and converts it into actionable insights – same as a cook who transforms ordinary products into an exclusive dish. With the scanning process completed, Sonar organizes vulnerabilities by severity levels so as to address high-risk assets first and plan the treatment of those at lower risk later on.
Detailed Reporting: Comprehensive reports are attached to every scan and list down the vulnerabilities found in the network, the locations in the network where those vulnerabilities were identified and also the consequences that may be caused by the exploitation of such vulnerabilities in a network. This helps in passing messages on the hierarchy and importance of alternate projects within the IT networks.
The software cumulatively also builds itself up to date response to constructs of threats that are evolving Mr Tawanda. For one informs then the software changes as new bugs come out and evenus. This makes the software comprehensive in addressing any problems related to networks.
Therefore, the combination of an effective scanning solution and an advanced data analysis process provides institutions with a more proactive protection mechanism against threats, leading to the improvement of the overall network security architecture of these companies. This introductory conception is designed to shield properties from damage, and bolster the confidence of the institutions in terms of risk management. safeguard sensitive information effectively.
Types of Vulnerabilities Detected
Common Security Issues
Many businesses today are moving in the direction of digitization, which brings along a lot of cyber problems to be faced. Unlike other services which try to fix each and every single issue, Sonar Software identifies the most common vulnerabilities that cause most of the businesses to fail. Some of the well-known vulnerabilities include:
Simple User Passwords: Some individuals do not surprise me at all in that so many companies have been broken into many piecemeal sections because someone used a simple easy-to-guess password. Here users can be informed and shown their accounts with default passwords which engagement people into taking new harder passwords.
Operating Systems Upgrades: Some organizations despite the far reaching recommendations by various ITC experts, still do not really care in terms of upgrading their systems. A software is run against the same standards and positive markers to identify the software that does not meet the support standard or is likely to have vulnerabilities.
Configuration Errors: Even though it is in every organization’s best interests to set up and manage a dedicated security measure to secure its networks, there are industries in the information industry for various reasons which do not. That is, regardless of whether there are erroneously configured open services and ports or permissive use of firewall – rule base is evident; the system employs some corrective features.
Once I recall situation which happened in the organization where I was previously employed, an incident where the organization lossignificant data breach due to a single outdated application. This event highlighted the significance of actively managing vulnerabilities.
You May Like: Master Zero-Day Vulnerabilities: 5 Key Risks, Detection Methods, and Prevention Tips
Advanced Threats
Yet it is not only the most elementary vulnerabilities to worry about as the more sophisticated kinds of attacks are even more challenging and call for specific detection methods to protect businesses in the most effective manner. Recognizing these sophisticated vulnerabilities of the Web application is where Sonar Software shows the greatest performance:
- Zero-Day Vulnerabilities: These are newfound vulnerabilities in software that don’t yet have a patch available. Sonar keeps pace with emerging threats, providing alerts even before patches are issued, giving organizations crucial time to mitigate risks.
- Advanced Persistent Threats (APTs): APTs involve coordinated attacks that infiltrate networks stealthily and remain undetected for prolonged periods. Sonar’s continuous monitoring capabilities enable the identification of unusual patterns indicative of such attacks.
- Ransomware Vulnerabilities: The emergence of ransomware has forced organizations to re-evaluate their security measures. Sonar can help identify weaknesses that make systems susceptible to these malicious attacks, ensuring that preventive measures are in place.
These advanced threats illustrate the necessity for continuous vigilance in network security. By leveraging Sonar Software’s robust detection capabilities, organizations can not only protect against common vulnerabilities but also fortify themselves against the sophisticated tactics employed by malicious actors today. In this ever-evolving landscape, staying informed and prepared is the key to maintaining strong defenses.
Real-Time Monitoring Capabilities
Instant Alert System
Highlighting the ever-growing need for companies to defend themselves against mundane and high-level weaknesses, emphasized in real-time monitoring analytics of the fraud prevention landscape. When considering the exemplary Sonar Software, a remarkable feature unique to it is the presence of an Instant Alert System eng; with real-time notifications to alert about such threats even as they surface. Just consider this: you can be sitting in a meeting, busy strategizing about the next big projects in the company, when you suddenly hear an alert sound from your digital device, since an internet security alert has been flashed. This could also mean the difference between intervention immediately or waiting until there is a significant amount of damage. The Instant Alert System is also set up in such a way as to keep you updated with real-time alerts regarding:
- Anomalous Activity: If any device shows unusual behavior that deviates from its typical patterns, Sonar will send an instant alert, signaling the need for further investigation.
- New Vulnerabilities Found: As scans are performed, and new vulnerabilities are identified, users receive instant updates, allowing for immediate remediation efforts.
- Critical Threshold Reached: Should any security metrics reach predefined critical levels, alerts are triggered, prompting teams to take swift action before issues arise.
In my previous role, we faced an incident where this alert system proved invaluable. An immediate notification about unusual bandwidth usage led to the discovery of a critical compromise before any data was lost.
Continuous Monitoring Features
Alongside the Instant Alert System, Sonar’s Continuous Monitoring Features offer an uninterrupted safety net for network environments. Unlike traditional scan-and-done strategies, continuous monitoring actively surveils networks 24/7, ensuring that potential vulnerabilities do not go unnoticed. Here’s what continuous monitoring encompasses:
- Ongoing Assessments: Automated, regular assessments analyze the network on an ongoing basis, providing insights that evolve alongside the threat landscape.
- Real-Time Configuration Checks: Continuous checks on firewall settings, user permissions, and system profiles ensure that any misconfiguration or deviation is detected immediately.
- Adaptive Threat Intelligence: By leveraging machine learning and threat intelligence, Sonar can adjust monitoring protocols based on emerging threats, making sure organizations are always one step ahead.
With these advanced real-time monitoring capabilities in place, organizations can foster a vigilant security posture. This proactive approach not only mitigates potential attacks but also builds trust—letting clients and stakeholders know that security is a top priority. By utilizing the robust tools that Sonar Software offers, businesses can take significant strides toward ensuring the integrity and safety of their digital environments.
Integration with Other Security Tools
Compatibility with Firewalls
As organizations bolster their security frameworks, integrating tools like Sonar Software with existing systems becomes essential. One of the key integration points is compatibility with firewalls, which play a critical role in defending against unauthorized access. By working seamlessly with firewall systems, Sonar enhances overall network security, creating a robust defensive layer. Here’s how this integration benefits organizations:
- Unified Threat Management: Sonar’s ability to communicate with firewall systems allows for real-time information exchange. When Sonar identifies a vulnerability, it can trigger firewall rules to block potential threats instantly.
- Enhanced Visibility: Integrating with firewalls provides a comprehensive view of incoming and outgoing traffic. This unified data stream allows teams to better understand potential attack vectors.
- Tailored Firewall Configurations: By analyzing security events detected by Sonar, organizations can adjust their firewall settings more effectively, ensuring they are optimized to respond against the most pertinent threats.
In a past project, we implemented Sonar alongside our existing firewall infrastructure. The immediate improvement in our security posture was evident as our firewalls began blocking malicious traffic that had previously slipped through unnoticed.
Collaboration with Antivirus Software
In addition to firewall compatibility, Sonar Software’s collaboration with antivirus solutions is another critical integration that strengthens an organization’s defenses. While antivirus software primarily focuses on detecting and eliminating malware, Sonar complements this by identifying vulnerabilities that could be exploited. Consider the following advantages of this collaboration:
- Comprehensive Threat Detection: By using both Sonar and antivirus tools, organizations can achieve a layered approach to security. Sonar identifies the gaps in security that antivirus may not address by focusing primarily on known malware signatures.
- Automated Responses: When Sonar detects a vulnerability, it can work in conjunction with antivirus software to initiate automated responses. For example, if a vulnerability relates to a specific exploit, the antivirus can increase its monitoring or apply remedial measures immediately.
- Actionable Insights: The data collected by Sonar can inform antivirus software about the evolving threat landscape. This enables the antivirus solution to update its databases and respond quickly to new threats.
With personal experiences to draw from, we witnessed how synergizing Sonar with our antivirus programs dramatically improved our threat detection capabilities while reducing response times. In conclusion, by integrating Sonar Software with firewalls and antivirus solutions, organizations can create a more cohesive and comprehensive security environment. Each tool plays its part in the puzzle, ensuring that vulnerabilities are identified, threats are mitigated, and organizational data remains safeguarded. This holistic approach to security not only fortifies defenses but also instills confidence among stakeholders and clients alike.
Benefits of Using Sonar Software
Enhanced Network Security
As organizations navigate the ever-evolving landscape of cyber threats, the implementation of Sonar Software offers significant advantages, most notably in enhancing network security. By proactively identifying vulnerabilities and providing real-time monitoring, Sonar delivers a fortified defense against potential attacks. Here’s how Sonar strengthens network security:
- Comprehensive Vulnerability Detection: Sonar’s ability to scan networks thoroughly ensures that all potential entry points are assessed, from servers to IoT devices. This comprehensive coverage translates into fewer blind spots, making it difficult for attackers to exploit weaknesses.
- Continuous Monitoring: The continuous monitoring feature allows organizations to remain vigilant. Real-time alerts concerning suspicious activities enable immediate responses, reducing the likelihood of a successful breach.
- Regulatory Compliance: For businesses operating in regulated industries, maintaining compliance is crucial. Sonar aids in identifying vulnerabilities that might violate compliance standards, helping organizations avoid penalties and maintain industry reputation.
I recall a situation in my previous role where Sonar uncovered a misconfigured device that could have led to a significant data breach. By addressing this issue promptly, we not only secured our data but also maintained our clients’ trust.
Time and Cost Efficiency
Another compelling benefit of using Sonar Software is the remarkable time and cost efficiency it provides. As businesses seek to optimize their operations and reduce security expenditure, Sonar’s capabilities align perfectly with these goals. Consider the following aspects of time and cost efficiency:
- Automated Processes: Sonar automates vulnerability scans and monitoring, drastically reducing the time IT teams spend on manual checks. This automation allows security personnel to focus on remediation rather than detection, streamlining workflows and freeing up valuable resources.
- Reduced Incident Costs: By identifying vulnerabilities before they can be exploited, Sonar minimizes the costs associated with security breaches, such as data recovery, legal fees, and reputational damage. Early detection ultimately translates into financial savings over time.
- As organizations increase in size, their security requirements also grow. Sonar is scalable, making it easy to integrate additional sensors and monitoring capabilities without convoluted deployments or significant sunk costs.
Drawing on a previous experience, one organization saw a 30% reduction in their security-related labor hours after implementing Sonar. This cross-cutting efficiency allowed them to allocate resources to other critical areas, driving innovation and growth. In summary, the integration of Sonar Software not only fortifies network security but also enhances operational efficiency while delivering substantial time and cost savings. For any organization, adopting such a proactive and comprehensive approach to cybersecurity is a wise investment in the face of an unpredictable digital landscape.
You May Like: Coalition Cyber Insurance: How Technology Is Changing Risk Management
Case Studies of Successful Vulnerability Detection
Enterprise Use Cases
In the realm of cybersecurity, leveraging robust tools like Sonar Software is essential for large enterprises that face complex security challenges. One compelling case involves a multinational corporation in the finance sector, which managed to significantly enhance its security posture using Sonar. This enterprise implemented Sonar Software to conduct thorough vulnerability assessments across its extensive network infrastructure. The initial scan revealed several critical vulnerabilities, including:
- Unpatched Software: Many corporate applications were running outdated versions, exposing the organization to known exploits.
- Poor Network Segmentation: Sonar identified areas where sensitive data was inadequately isolated, leading to potential exposure from less secure segments.
Based on these findings, the firm implemented immediate remediation measures, including patch deployment and enhanced segmentation protocols. As a result, they experienced a 40% reduction in security incidents over the following year, earning praise from stakeholders for their commitment to securing sensitive financial data.
Small Business Applications
While large enterprises often dominate security discussions, small businesses can equally Sonar is one of the tools that saw its popularity skyrocket. Among the numerous positive uses found is a case that happened in a local online retail store where most of the e-commerce firms are currently endangered by the rampant phishing attacks against latest target segments the company is serving. The solution was look into appropriate measures of boosting the security, as a consequence her calling on Sonar Company for vulnerability scanning. A success story was documented in the following terms:
Unearthing Weaknesses: Firstly, Sonar was able to show the marketing team where they were most exposed starting with inadequate password systems and ending with plugins that were more than a year old.
Looking ahead: In view of what the sonar technologies could (and should) bring, shifted awareness led to making certain adjustments in the organization’s information exposure and elegitimacy policy, changed the length limitations, and pressed for software updates in any which wider interests would have stood to suffer without them.
In less than three months, the organization was down at the drawing board to explain to it’s audience about the heightened security precautions taken since raised customer confidence. The shopkeeper further realized that there were marked reductions in the card related costs of protecting the systems since they were able to prevent the occurrence of any major intrusions. Wrapping up the types of businesses, these examples depict how effective Sonar is in security scanning since the above cases are applicable in all in-house Computer Systems installations. Every organization, irrespective of size of the threat, has security concerns to attend to during operations and in data management ion compassing the use of people.
Future Developments in Sonar Technology
Machine Learning Integration
As the landscape of cybersecurity continues to evolve, so too does the technology that underpins it. One of the most exciting developments on the horizon for Sonar Software is the integration of machine learning capabilities. This advancement has the potential to revolutionize how vulnerabilities are detected and addressed. Machine learning will enable Sonar to:
- Enhance Predictive Analysis: By analyzing historical data, Sonar can predict potential vulnerabilities before they become significant threats. This proactive approach means organizations can bolster their defenses even before issues arise.
- Improve Threat Detection: Machine learning algorithms can recognize patterns and anomalies in network behavior more effectively than traditional methods. This means Sonar will be better equipped to identify sophisticated threats, such as advanced persistent threats (APTs), which often go unnoticed by standard detection techniques.
- Automate Remediation: Imagine Sonar not only identifying a vulnerability but also automatically proposing or implementing patches based on past remediation practices. This could significantly reduce the response time for security threats.
In a personal experience, I recall working with a team that integrated machine learning algorithms into their security protocols. The results were astonishing, as the system became increasingly adept at identifying and mitigating threats over time, leaving the team free to focus on strategic initiatives.
Expansion into IoT Security
Alongside machine learning, the expansion of Sonar Software into the realm of IoT security isAn equally extremely notable change. Due to the widespread use of Internet of Things (IoT) devices in business as well as homes to some extent, it is imprudent to overlook the possible weaknesses and their threat to such devices. Crafting operational policies and regulations for safeguarding Internet of Things and its vulnerabilities over time will make it possible for Sonar to:
To Identify Specific Device Risks: Unlike the conventional networking environment, IoT devices have its unique security issues. This would enable Sonar broaden its scope so that these problems can be overcomed such as insecurity through the default setting of the device or the lack of provision for security through sharing of credentials.
To Monitor Device Behavior: It is not usually enough to identify how the devices interact with each other or how they connect to network functionalities. Closely observing these interactions allows the detection of suspicious user behavior e.g. where certain devices behave in an abnormal way such as sending data to unusual destinations.
To Improve the control of devices: Where relevant, organizations will be offered alternate security vibration levels to be used in each of their IoT devices to ensure that they meet the set guidelines.
I know firsthand how important this area of the Internet of Things is today, as it also has quite an interesting history of development and usage in the security environment. An interesting aside was the infiltration of the heating system in one domestic system due to a security vulnerability in the smart thermostat connected to it. Thankfully, there’s a lot to look forward to in the next enhancements to the Sonar Software, including things like the inclusion of machine learning and more focus on securing IoT devices. With the changes of the current and future threats, Sonar has been able to upgrade and thus provide great guidance to its members. This strategy not only determines the location of the assets but conventions the user into a level of appreciation where risk has to be challenged.

