Key Differences Between IAM and PAM Solutions: A Comprehensive Comparison 2024
Understanding IAM and PAM Solutions In the realm of cybersecurity, it is imperative to manage the access to sensitive data streams. IAM and PAM are terms which are used to…
How Biotech Advances Could Impact Our Lives Sooner Than You Think In 2025
Overview of Biotechnology Biotechnology has paved a new frontier as far as technology is concerned in connecting important sectors and industries. Biotechnology at its core is manipulating materials made from…
Why New Tech Tools Are Making Life Easier (and What’s Next!)
We live in an age where we are constantly pressed for time. And use New/Old Tech Tools, in the given situation, purports to alter virtually all aspects of human existence.…
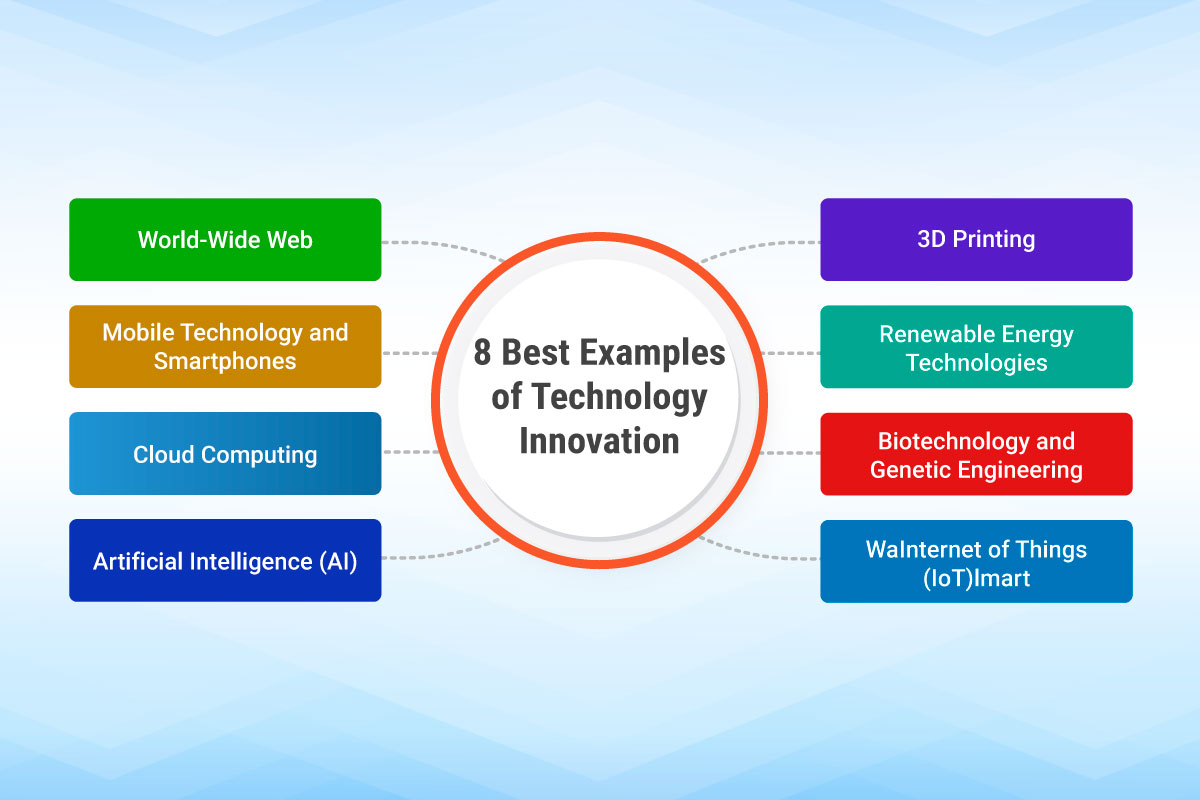
Innovation Strategies That Are Changing Tech as We Know It
Introduction The Importance of Innovation in Technology The use of new solutions and options in technology is not merely a trend; in today's world, it is the major limitation for…
Inside the SOC (Security Operations Center) How Threats Are Monitored and Managed
Introduction to Security Operations Centers (SOCs) Security threats increase as businesses improve their technology capacities because we live in a digital world. Because of this, a new concept was created…
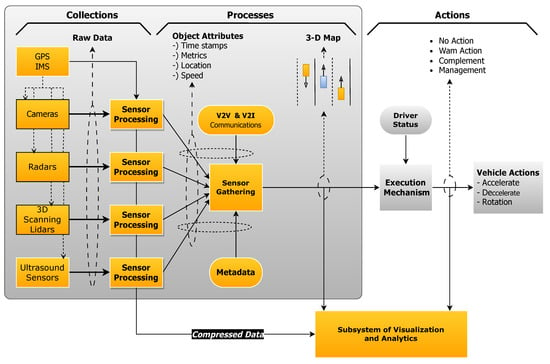
Why Cybersecurity is Non-Negotiable for the Safety of Autonomous Vehicles 2024
Introduction Overview of Autonomous Vehicles The power of the autonomous vehicle is really a paradigm shift in transportation. These are the vehicles that employ a suite of advanced integrated technologies,…
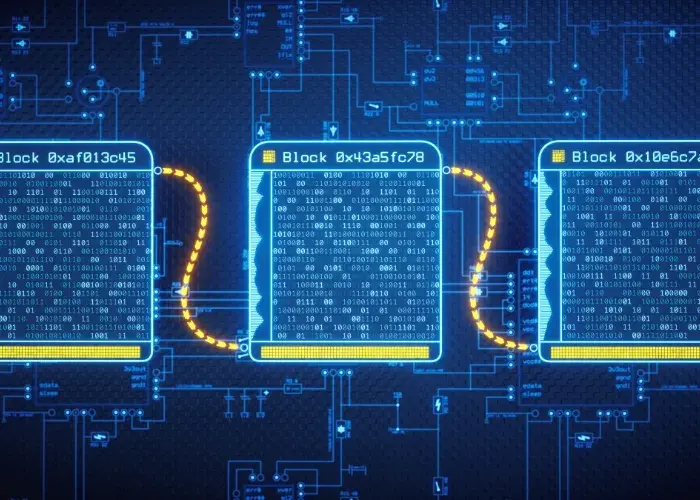
How Blockchain is Transforming Supply Chains and Logistics 2024
Introduction to Blockchain Technology Overview of Blockchain Indeed, Blockchain technologies changed the way we think about data. Actually, it is a kind of distributed digital ledger that maintains a record…
Say Goodbye to Passwords Biometrics Is Here: The Evolution of Biometrics in Security 2024
Introduction Overview of password-based security Password-based security stands out as the basis for the protection of personal and sensitive information throughout modern times. In popular usage, however, a number of…
Google Patches Critical Android Vulnerability Exploited by Spyware Makers 2024
Google Patches Addresses Active Exploitation of Android Vulnerability (CVE-2024-43093) Google has released patches for a serious Android vulnerability identified as CVE-2024-43093, which is reportedly being exploited in targeted attacks. This…
Critical Vulnerabilities Found in Ollama AI Framework: Risks of DoS, Model Poisoning, and Theft 2024
Vulnerabilities in Ollama AI Framework Cybersecurity researchers have revealed six significant vulnerabilities in the Ollama AI framework that could be exploited by malicious actors for a range of harmful activities,…