Inside the SOC (Security Operations Center) How Threats Are Monitored and Managed
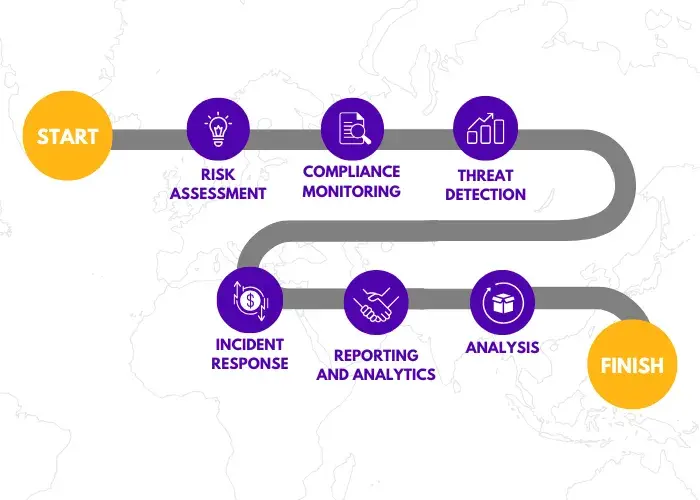
Introduction to Security Operations Centers (SOCs) Security threats increase as businesses improve…
Why Cybersecurity is Non-Negotiable for the Safety of Autonomous Vehicles 2024
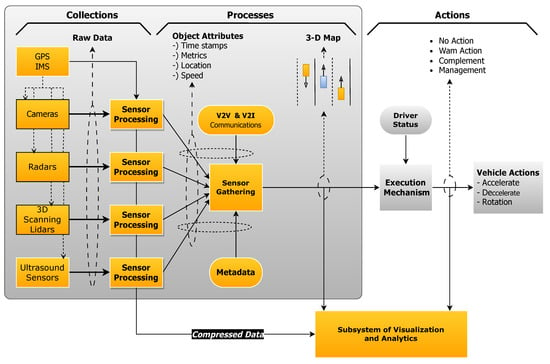
Introduction Overview of Autonomous Vehicles The power of the autonomous vehicle is…
How Blockchain is Transforming Supply Chains and Logistics 2024
Introduction to Blockchain Technology Overview of Blockchain Indeed, Blockchain technologies changed the…
Say Goodbye to Passwords Biometrics Is Here: The Evolution of Biometrics in Security 2024
Introduction Overview of password-based security Password-based security stands out as the basis…
Google Patches Critical Android Vulnerability Exploited by Spyware Makers 2024
Google Patches Addresses Active Exploitation of Android Vulnerability (CVE-2024-43093) Google has released…
Critical Vulnerabilities Found in Ollama AI Framework: Risks of DoS, Model Poisoning, and Theft 2024
Vulnerabilities in Ollama AI Framework Cybersecurity researchers have revealed six significant vulnerabilities…
The Ultimate List of Top 10 Open-Source Cybersecurity Tools for 2024
Introduction Importance of Open-Source Cybersecurity Tools In the fast-paced world of technology…
The Rise of Cloud Security Posture Management (CSPM): How to Protect Cloud Infrastructure 2024
Introduction Overview of Cloud Security Posture Management (CSPM) In today’s digital age,…
2024’s Ultimate Guide to Multi-Factor Authentication Best Practices
Introduction to Multi-Factor Authentication What is Multi-Factor Authentication? Multi-Factor Authentication (MFA) is…
Real-Time Vulnerability Detection with Sonar Software – Your Ultimate Defense 2024
Introduction Overview of Sonar Software In the days we are living in,…