GPL or Nulled? Navigating the Security Maze for WordPress Enthusiasts
Understanding GPL and Nulled in WordPress Definition of GPL It is indeed…
Understanding GPL License & Risks of Using Nulled WordPress Themes and Plugins
Understanding the GPL License A base for free software licenses is known…
Top 20 Cybersecurity Companies to Watch in 2024
Cybersecurity Companies With the continuous evolution of the cyberspace, the demand for…
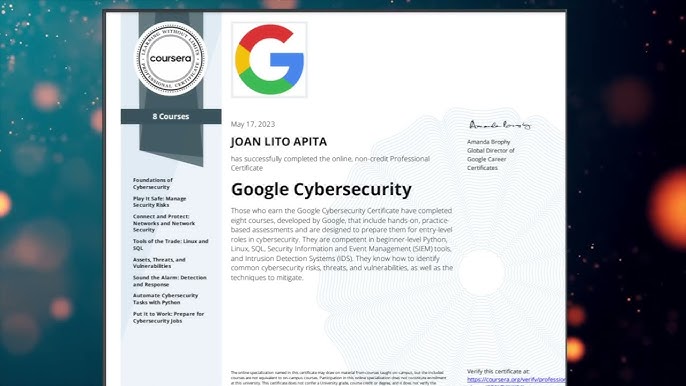
How to Get Google Cybersecurity Certified and Boost Your IT Career
Overview of Google Cybersecurity Certification In the context of pursuing career advancements…
How to Access the Deep Web with the TOR Browser in 2025 on Any Device
Browsing the deep web using the TOR browser Network is a well-known…
The Technology Behind GTA 5’s LSPDFR Mod
Summary of LSPDFR Mod in GTA V The LSPDFR modification of Grand…
Top Vulnerability Management Tools: Reviews & Comparisons
Top Vulnerability Management Tools: Reviews & Comparisons 2024 Ransomware is a significant…
Key Differences Between IAM & PAM Solutions: Comprehensive Comparison
Understanding IAM and PAM Solutions In the realm of cybersecurity, it is…
The Ultimate List of Top 10 Open-Source Cybersecurity Tools for 2024
Introduction Importance of Open-Source Cybersecurity Tools In the fast-paced world of technology…
Cost Management in Cloud Computing – Tips for Staying Within Budget
Introduction to Cloud Computing Cost Management Understanding Cost Management in the Cloud…