Have you ever had the wish of not sharing your real email address and still doing things on the internet? Business sites, such as 10-Minute Mail, make it very easy to create disposable email addresses that disappear after a short period. They’re quick, convenient, and wise to avoid spam or keep your privacy.
But, how anonymous are these services? Can they keep your personal details safe? Will they be traced back to you? This article is, therefore, investigating how such tools work, pros and cons associated with them, and information you need to utilize them in real-world applications.
What Is 10-Minute Mail?
10-Minute Mail is a free service where you make a temporary email address with a countdown of ten minutes. The time can be extended to 100 minutes, making the site versatile for short-term purposes. Here’s how it works:
- Create an email: Go to the 10-Minute Mail website and it will automatically create an email address.
- Use the email: Now use this email to get signed up for services or receive verification codes.
- Auto-delete: Once the time runs out, the email address and all its contents will be deleted.
It’s popular with people who don’t want to give one of their email addresses to third parties because it helps cut down on unwanted mail while offering some level of privacy. Their permanent email addresses with third-party platforms, reducing spam and maintaining privacy.
How to Use 10-Minute Mail: Stepwise
This is how absolutely simple the use of 10-Minute Mail, as well as many other temporary email services, is: step-by-step guidance.
1. Reach the site: Just go to the 10-Minute Mail site or some other one that suits you.
2. Get your temporary email: The site will automatically generate a temporary email address for you to use.
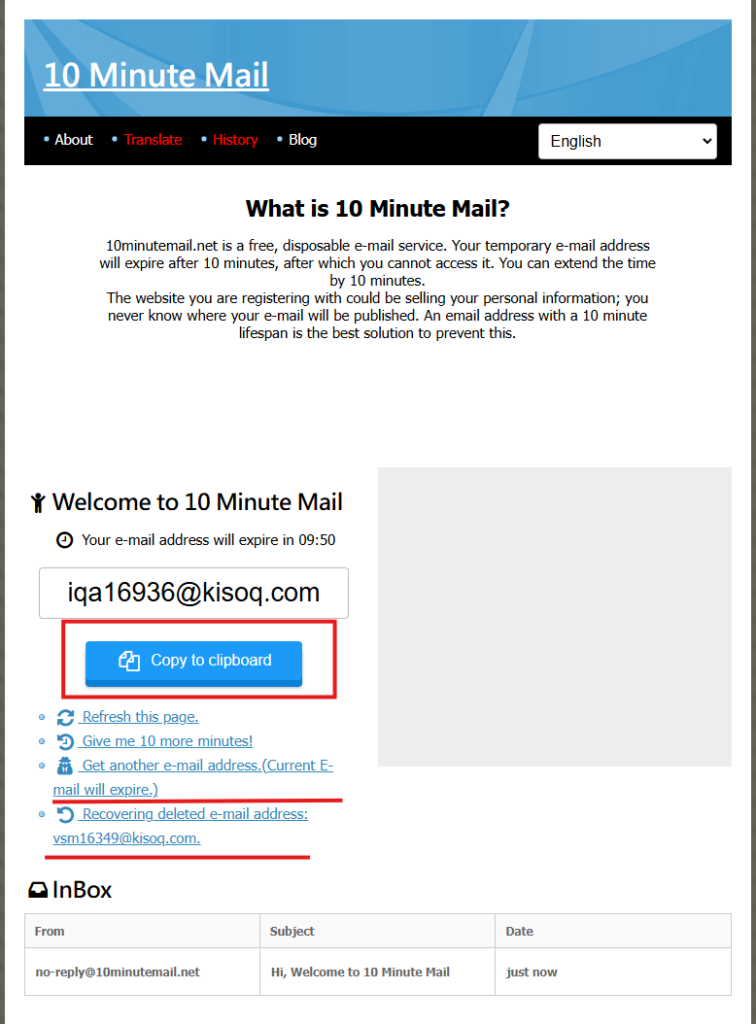
4. Auto-delete after 10 minutes: At the end of 10 minutes, the email address and all information related to it would be automatically deleted, thus ensuring your anonymity.
PRO TIP: Most temporary email services follow this procedure since they make it so user friendly and smooth that any customer can easily use it without much effort in tech.
How & Is Disposable 10 Minutes Mails Trackable ?
No, it’s not trackable. However, if you use the steps under "Best Practices for Using 10-Minute Mail", it will be 100% untraceable.
How Disposable 10 Minutes Mails Trackable?
1. IP Address Logging
10 Minute Mail logs usually have the IP addresses of users. The service is also independent of associating personal information with the temporary email address:
- Legal Requests: Government subpoenas in forcing such conditions can lead to the service provider making IP logs available.
- Using a VPN or Proxy: Through routing a connection with a VPN or proxy, one effectively masks an otherwise actual IP address, increasing the anonymity.
2. Metadata Storage
Some temporary email providers keep metadata like the time the email was created, the person it was sent to, and sender data. Although this does not directly reveal one’s identity, it could be used to:
- Identify patterns of usage.
- Cross-reference with other platform data.
3. Behavioral Patterns
When you keep using those temporary emails for registering for services concerned with personal identity, you can find patterns emerging, which can connect the main accounts. For example:
- Using temporary email for websites where you have used real names.
- Creating accounts requiring some other verifications concerning personal data.
4. Interactions with Third-Parties
Once a temporary email is used for registration in service, your privacy gets affected by the communication with the given service. Data depends on that platform’s policies. If the platform logs the email alongside identifiable user information, your anonymity might be compromised.
Is It Legal to Use 10-Minute Mail?
Legal Use Cases
To the general extent that 10-Minute Mail can be considered legal, this tends to be true in most jurisdictions. The service is meant for the following legitimate purposes:
- Safeguarding Privacy: Not subjecting an email account to spam and protecting personal email accounts.
- Single-use: For example, sign up for a free trial or confirm a verification code.
- Anonymous: Maintain anonymity when interfacing with unknown portals.
Illegal or Questionable Use Cases
In some circumstances, the use of 10 Minute Mail could breach laws or terms of service:
- Fraud: Misleading use of short-term emails for deception or fraud may also involve punishments by law.
- Violation of Platform Terms: Most websites specifically prevent the use of disposable emails to deter abuse. Violation of this term may lead to account bans or other possible penalties.
- Prohibited Countries: Some nations have laws on anonymizing services, including temporary email services.
Consequences of Misuse
- Legal Actions: Your illegal activities can be traced all the way back to you with your temporary email.
- Service Restrictions: A service might ban the use of disposable email and tag the account as disabled thus preventing access.
Real-Life Scenarios
Case 1: Avoiding Spam
John wants to download an eBook without spending a penny but must provide an email address. He uses a 10-Minute Mail service to avoid any crap in his primary mailbox. In the present case, John preserves anonymity because the eBook provider does not require other identifiable information.
Case 2: Banned Platforms
Sarah uses 10-Minute Mail mainly for signing up on survey platforms. With time, the platforms tend to realize and ban disposable email addresses. Here, Sarah’s act is not tracked by 10-Minute Mail but by the systems of the survey platforms.
Case 3: Legal Investigations
A user carries out fraudulent activities using 10-Minute Mail. Upon inquiry, the authorities wish to get IP logs of the service provider. If the user did not use a VPN, it would lead to his real IP address being traced.
Best Practices for Using 10-Minute Mail
- Being Safe from Public Access: Run your connection through a VPN or the Tor Network to conceal your IP address.
- Linking Personal Data: Do not use temporary emails for accounts where real personal information is expected.
- Know Platform Policy: Awareness of how the sites you visit handle emails is important.
- Try Alternatives On Account of Long-Term Anonymity: Available encrypted email providers, such as ProtonMail, are for those who want long-term safety.
Alternatives to 10-Minute Mail
| Service | Features | Free/Paid |
|---|---|---|
| Guerrilla Mail | Offers address scrambling and the ability to send emails. | Free |
| ProtonMail | Provides end-to-end encryption and a zero-access guarantee. | Free/Paid |
| Temp-Mail.org | Offers disposable emails with a user-friendly mobile app. | Free |
Security Limitations of 10-Minute Mail
10-Minute Mail offers basic anonymity, but it does not have the best security features such as encryption or user authentication. Here are some limitations:
- No Encryption: Emails are unencrypted, which makes them easy for interception.
- Limited Support: Minimal customer support is provided while the user is being lured to sign up using simplicity.
- Temporary Nature: Deleted e-mail inboxes may remain retrievable for a while, but not in a long period of time.
Lastly
10-Minute Mail is good for private communications and spam prevention but is not entirely trace-less. Understanding its limitations and practicing the recommended methods will maximize user confidentiality. Some alternatives for stronger privacy are ProtonMail or Guerrilla Mail, which have upgraded features.
A temporary email service comes to your rescue either way-whether you want to use it for signing up against a single service or want a protection service for the longer run. Always know what you are getting into before trying out temporary email services so that you make informed decisions. And above all, be vigilant about online security.