when searched for vpn vs tor vs proxy, you’re probably trying to figure out which tool will actually solve your problem: hide your browsing from a flaky cafeeh Wi-Fi, access Netflix from another country, or protect your identity while researching something sensitive. This article explains the difference, when to use each, and how I tested them in real life so you get practical.
This isn’t a legal advice i recommend to always check local laws about VPN/Proxy/Tor use!!
Fast Answer – for those who don t like to read
Here’s the thing: all three tools change the path of your internet traffic, but they do very different jobs.

- Virtual private network is basically a private tunnel. Your internet traffic leaves your laptop or phone, goes into that tunnel, and pops out on the VPN company’s server. Your internet provider only sees you connected to the tunnel — not the actual sites you’re visiting — and the websites just see the VPN’s IP address, not yours.
- Tor works differently. Instead of one tunnel, it bounces your traffic through a chain of random volunteers’ servers, like passing notes down a line of strangers. Each one only knows who handed it the note and who it’s passing it to, but nobody along the way has the full picture. That’s what gives Tor its anonymity, though it comes at the cost of speed.
- Proxy is the simplest of the three. Think of it as a middleman that just grabs something from the internet and hands it to you. It works for one app or one type of traffic at a time. It doesn’t really hide much, and unless you’re using HTTPS, it won’t even encrypt your connection.
What I did and what happened
I spent an afternoon on a busy coffee shop Wi-Fi doing three tasks: watch a geo-locked video, research a sensitive topic without leaving traces, and run a small scraping script for a personal project. I tried a paid virtual private network, Tor Browser, and a SOCKS proxy, all on the same laptop.
VPN: Streaming worked; speeds were fine, hid my activity from the cafeh network but I realized I was swapping trust from the ISP to the Virtual private network provider. I checked the virtual private networks privacy policy and noted they said they didnt log connection data (I didnt dig further so thats an assumption on my part and should be verified).
Tor: I used Tor Browser for the sensitive browsing. Pages were slower, some media broke, but it felt right for anonymity.
Important note: sites that require JavaScript-heavy logins often didnt behave; and many streaming services block Tor exit ips.
SOCKS proxy: It was a convenient way to route the scraper traffic. Fast enough. But a few target endpoints flagged the proxy IP and returned captchas proxies are easy to detect and block.
What this really means is for daily speed and convenience = pick a VPN; for true anonymity, use Tor and for targeted app-specific routing, use a proxy / but know the limitations.
Difference between VPN vs Tor vs Proxy
VPN
VPN sets up a tunnel from your device to a remote server controlled by the Virtual private network provider. From the outside, websites see the Virtual private network server’s IP — not your home IP. Your ISP can see you’re connected to a Virtual private network but not the pages you visit (they see encrypted traffic). That’s great for hiding browsing on public Wi-Fi and for unblocking region-locked content.
Which tools I’d actually like: people always ask, “Okay, but which VPN should I use?” Here’s the thing: I can’t give you a magic answer because it depends on budget and threat model, but I’ll at least point you toward a few I’ve tested or researched. ProtonVPN and Mullvad are solid because they’ve had independent audits and a reputation for not playing games with logs. NordVPN is bigger, works with Netflix more often, but you’re trusting a bigger company. None of these are perfect / check their policies yourself.
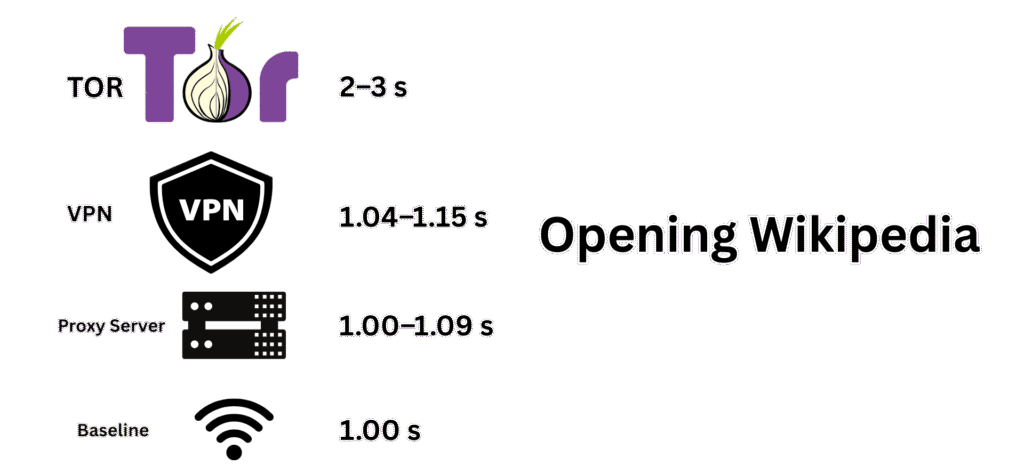
How much speed you really lose: numbers stick better than “it felt slow.” In my quick cafeeh test, the VPN dropped my speed maybe 3.8–15%. Tor was way heavier – pages took two or three times longer to load. plain proxy barely slowed things down at all, but it also didn’t give me encryption, so that trade-off was obvious.
Important caveat: Virtual private network provider can see and (if they wanted) log your traffic. So provider reputation, privacy policy, and audits matter. (needs citation)
Tor
Tor sends your traffic through at least three relays: entry (guard), middle, and exit. Each relay only knows its neighbor, so no single hop knows both your IP and the destination site. That’s why The Onion Router is the right tool when your goal is anonymity, not just privacy.
The “is this even legal?” question: most of the time, yes. Using a VPN, Tor, or a proxy isn’t a crime. Misusing them for shady stuff is. Some countries (like China, Russia, Iran) heavily restrict or block these tools, so check your local rules before assuming.
But it’s slower, some sites block Tor, and exit nodes can see unencrypted traffic – so always use HTTPS over Tor.
Proxy
A proxy stands between your app and the destination. HTTP proxies are commonly used for web traffic; SOCKS proxies are lower-level and handle many protocols. Proxies don’t inherently provide encryption — you rely on the app’s protocol (HTTPS) for that. They’re good for app-specific tasks (scraping, testing) but not a full privacy solution.
| Feature | VPN | Tor | Proxy (HTTP / SOCKS) |
|---|---|---|---|
| Encrypts traffic to the next hop? | Yes | Yes (layered) | Only if the app uses HTTPS |
| Hides destination from local network? | Mostly | Yes (to some extent) | Not reliably |
| Best for | Streaming, general privacy | Strong anonymity, sensitive browsing | One-app or lightweight IP routing |
| Typical speed | Moderate | Slowest | Often fastest |
| Who you must trust | Virtual Private Network provider | No single relay (but exit node risks) | Proxy operator |
| Setup difficulty | Easy | Easy for browser, advanced for system | Very easy |
You May Like To Read: BackBox Linux vs. BlackArch Linux vs. ArchStrike – Full Breakdown In 2025
Pick what fits your need
If you want speed and streaming or gaming:
Choose a VPN. It preserves bandwidth better than The Onion Router, and it’s compatible with streaming services when you pick a provider that isn’t blocked by CDNs. Steps:
- Pick a reputable Virtual Private Network with a clear policy (look for audits). (needs citation)
- Enable the kill switch.
- Connect to a nearby server or a server in the country you need.
If you need strong anonymity:
Use Tor. Steps:
- Download Tor Browser from the official site.
- Don’t log into accounts tied to your real identity.
- Avoid downloading files over The Onion Router when possible, because files can contain deanonymizing content.
If you just need one app to appear from another IP:
Use a proxy. Steps:
- Choose between HTTP and SOCKS depending on the app.
- Configure the app or system proxy settings.
- Expect some sites to flag known procuration or authorization to act for another IPs.
You May Like To Read: Linux Mint vs Ubuntu — Which Desktop Linux Should You Pick?
Step-By-Step – Apply And Install
for Virtual Private Network for e.g. If you pick NordVPN, go to their site, sign up with an email you check, then download the installer for your OS and run it – you’ll get a prompt to log in. Once you’re in the app, flip on the kill-switch and DNS leak protection so your traffic doesn’t sneak out if the Virtual Private Network drops, and pick the WireGuard (or Lightway) option if speed matters to you (WireGuard is usually faster, but check the provider docs). Connect to a server in the country you need for streaming and test one site — if it blocks you, try a different server or the provider’s stealth/obfuscation option. Set the client to start with your computer if you want constant protection, keep it updated (small updates often patch leaks)
& For Tor, only ever download onion router Browser from torproject.org, open it, and treat it like a separate persona: don’t log into accounts tied to your real name, don’t add extensions, and don’t mix it up with your normal browsing. Use the security slider if a site breaks – bump it up a notch and things that rely on heavy JavaScript will stop working, which is annoying but sometimes necessary. If Tor is blocked where you are, use the bridge settings in the browser; on Android you can use Orbot, on iPhone look for an Onion-capable browser.
If you want to use proxy for a single app, decide whether you’ll rent a SOCKS5 or run your own SSH tunnel from a server you control — both work. To run your own, open a terminal and type ssh -D 1080 user@yourserver and that creates a local SOCKS proxy at localhost:1080; point your browser or app at that address. For scripts, point the library to socks5h://127.0.0.1:1080 (in Python, for example, you’d set proxies={'http':'socks5h://127.0.0.1:1080','https':'socks5h://127.0.0.1:1080'}). Remember: proxies don’t magically encrypt everything { HTTPS still matters } and some sites will flag proxy IPs or throw captchas at you (needs citation). Use proxies for short, one-app jobs; don’t expect them to be a device-wide privacy fix.
Quick myth (because I see these all the time)
- “VPN = anonymity” Not true. Virtual private networks hide your traffic from the local network, but they shift trust to the Virtual Private Network provider. (needs citation)
- “Tor is only for criminals” No. The Onion Router is used by researchers, journalists, and ordinary people who want privacy. The association with criminality is a bias, not a technical definition.
(who to trust vs. what you hide)
| Threat / Adversary | VPN helps hide from | Tor helps hide from | Proxy helps hide from |
|---|---|---|---|
| Local Wi-Fi snooping | Yes | Partially (ISP still sees Tor usage) | No (unless encrypted) |
| Content provider (website) | Hides your IP (site sees VPN IP) | Hides your IP (exit node IP visible) | Hides IP (site sees proxy IP) |
| virtual private network provider itself | — | The Onion Router helps (doesn’t rely on provider) | Proxy operator can see traffic |
| Global intercept (advanced) | Depends on logs + jurisdiction (needs citation) | Stronger, but not perfect | Weak |
When to use which
| You want to… | Use this |
|---|---|
| Watch Netflix from another country | Virtual Private Network (if provider works with the service) |
| Browse anonymously about sensitive topics | Tor Browser |
| Run a one-off script from a different IP | procuration or authorization to act for another or Virtual private network depending on speed needs |
| Protect all your device traffic on public Wi-Fi | Virtual Private Network |
Risks & common pitfalls (don’t skip these)
- Trusting providers blindly. Read the privacy policy. Look for audits and independent reporting. (needs citation)
- Exit node interception (onion router). Unencrypted traffic can be seen by exit nodes. Use HTTPS.
- Service blocking. Many sites block The Onion Router and known Virtual Private Network/proxy IP ranges. If you need reliability, you might have to switch providers or use residential proxies (residential IPs are another area with separate risks). (needs citation)
- False sense of security. No tool replaces good hygiene: strong passwords, 2FA, HTTPS, and being careful with downloads.
You May Like To Read: Kali Linux vs Parrot OS: 5 Major Differences That Impact Your Security
How to decide, now
Virtual private network for day-to-day privacy and streaming. onion router for tasks that require real anonymity. procuration or authorization to act for another when you only need to reroute one app. In simple terms: choose the tool that matches the threat you’re worried about, not the one that sounds best in a forum.
I used these tools myself in a real public-Wi-Fi test and noted the trade-offs above. If you want, I’ll now go sleep.